Restrict device access with 1Password Extended Access Management (XAM)
Last validated:
1Password Extended Access Management (previously, Kolide) collects a series of signals from its agent installed on each device that can be used to determine the security posture of a device. Tailscale can fetch these signals from XAM and use them as device posture attributes in access rules, which can then be used by organizations to grant access to sensitive resources only to devices that have a high level of trust.
You can achieve this Tailscale's device posture management features:
- Device Identity Collection, which collects identifiers (for example, serial numbers), used to match devices in Tailscale to devices in XAM.
- XAM posture integration, which synchronizes signals from XAM to device posture attributes in Tailscale.
- Posture conditions in access rules, which lets you configure access restrictions based on device attributes.
This guide explains how to enable Device Identity collection for your Tailscale network (tailnet) and configure XAM posture integration.
What is 1Password XAM (Kolide) posture integration?
The 1Password XAM (Kolide) integration syncs data between XAM and Tailscale on a recurring schedule. During each sync, Tailscale performs the following actions:
- Fetches a list of hosts and their reported data from your XAM account.
- Matches XAM devices to devices in your tailnet based on serial numbers.
- Writes the XAM data to device posture attributes on each matched device.
The integration writes the following device posture attributes to matched devices:
| Attribute key | Description | Allowed values |
|---|---|---|
kolide:authState | Authorization status of the device | Good, Notified, Will Block, Blocked |
Prerequisites
Before you can set up the 1Password XAM (Kolide) integration, make sure you have:
- Device Identity Collection enabled, and devices in your tailnet are reporting identifiers.
- A 1Password XAM (Kolide) account for which you have permission to create an API token.
Create 1Password XAM (Kolide) API Key
To authenticate your 1Password XAM (Kolide) account with Tailscale, you'll need to create a 1Password XAM (Kolide) API Key. The 1Password XAM (Kolide) integration uses these to fetch a list of devices and their data from 1Password XAM (Kolide).
To create a 1Password XAM (Kolide) API Key:
-
Select your user avatar in the upper-right corner of the 1Password XAM (Kolide) UI.
-
In the dropdown menu, select Settings.
-
In the menu on the left, select Developers.
-
In the sub-menu that appears, select API Keys.
-
On the next screen, select Create New Key.
-
In the modal that appears, provide a name for the Key and the name of a XAM administrator who will be responsible for the API Key's usage, and select Save.
-
Once saved, the secret token is available in the table. Select the duplicate button to copy the token to your clipboard.
Configure 1Password XAM (Kolide) posture integration
To configure Tailscale to fetch data about devices from 1Password XAM (Kolide):
-
Open the Device management page of the Tailscale admin console.
-
Under the Device Posture Integrations section, locate the 1Password XAM (Kolide) integration, then select Connect.
-
Enter your API Key.

-
Select Connect to 1Password XAM (Kolide).
Review the integration status
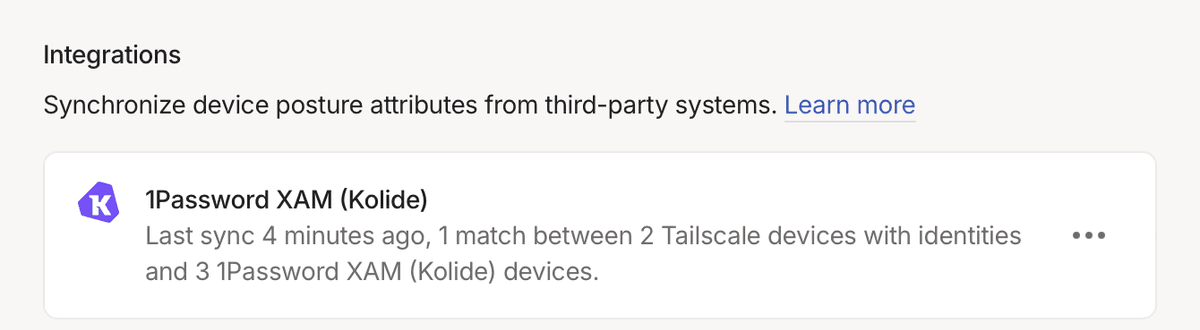
Next, check to ensure the 1Password XAM (Kolide) integration has run successfully.
- Go to the Device Posture Integrations section of the Device management page.
- Locate the 1Password XAM (Kolide) integration under the Integrations section.
After the 1Password XAM (Kolide) integration runs successfully, it shows the time of the most recent sync, the number of synced devices, and any errors that occurred while synchronizing.≈
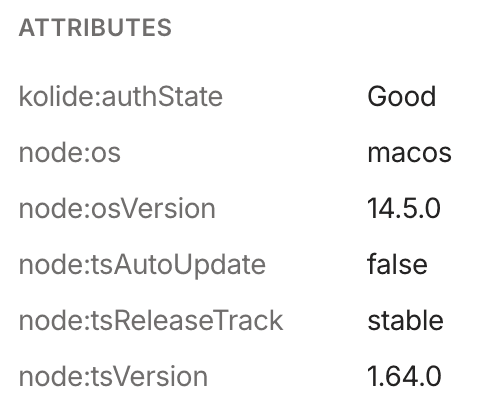
Check node attributes
After you set up the 1Password XAM (Kolide) integration, you can confirm that Tailscale is writing the new node attributes for your 1Password XAM (Kolide) devices from the Tailscale admin console.
- Open the Machines page of the Tailscale admin console.
- Select a device to inspect.
- The node attributes for the device are in the Machine Details section. This should include the set of
kolide:attributes listed previously.
You can also check device attributes using the Tailscale API.
Adjust Tailscale access rules
After you set up the 1Password XAM (Kolide) posture integration, and your devices have device posture attributes that reflect their signals as reported by 1Password XAM (Kolide), you can use those device posture attributes as part of your posture rules.
For example, to only permit access to tag:production from devices that are reported as good by the 1Password XAM (Kolide) agent, you can create a new posture and use it as part of a corresponding access rule:
"postures": {
"posture:trusted": [
"kolide:authState != 'Blocked'",
],
},
"grants": [
{
"src": ["autogroup:member"],
"dst": ["tag:production"],
"ip": ["*"],
"srcPosture": ["posture:trusted"]
}
]
You can use the visual policy editor to manage your tailnet policy file. Refer to the visual editor reference for guidance on using the visual editor.
Schedule
For each configured integration, Tailscale will aim to sync device posture attributes every 15 minutes, with a few exceptions:
- Adding a new integration, or changing configuration of an existing one, will trigger an out-of-schedule sync.
- If an integration fails due to authentication error (usually caused by invalid credentials), it will be paused for up to 24 hours.
Audit log events
The following audit log events are added for device posture.
| Target | Action | Description |
|---|---|---|
| Integration | Create posture integration | A new posture integration was created |
| Integration | Update posture integration | A posture integration was updated |
| Integration | Removed posture integration | A posture integration was removed |
| Node | Update node attribute | Device posture attributes for a node were changed |
