Ephemeral nodes
Ephemeral nodes make it easier to connect and then clean up short-lived devices such as containers, cloud functions, or CI/CD systems that spin up and spin down on a regular basis.
By default, when you add a new device to your Tailscale network, it appears in your admin console and in Tailscale client apps. However, short-lived devices can make your network difficult to navigate, as devices remain in the admin console until removed.
Ephemeral nodes differ from regular nodes in a few ways:
- They are auto-removed from your network after a short period of inactivity. The next time an ephemeral node is created, it will have a new IP address.
- They are immediately removed from your network if you run
tailscale logout. - They can only be created using ephemeral auth keys (not through the regular authentication flow) or by running the
tailscaleddaemon with thestate=mem:flag.
To avoid updating every device's netmap when an ephemeral device is added to the Tailscale network, consider using an ephemeral tagged auth key, and update access control policies to restrict what tagged devices can access. If you are deploying multiple instances of the same container, use a reusable auth key instead of baking the Tailscale node key into the container image to avoid duplicate devices.
You can identify ephemeral nodes in your admin console by looking for an "Ephemeral" badge underneath the device name.
Authenticating an ephemeral node
Step 1: Generate an ephemeral auth key
To create an ephemeral node, you'll first need to generate an ephemeral auth key from the auth keys page of the admin console.
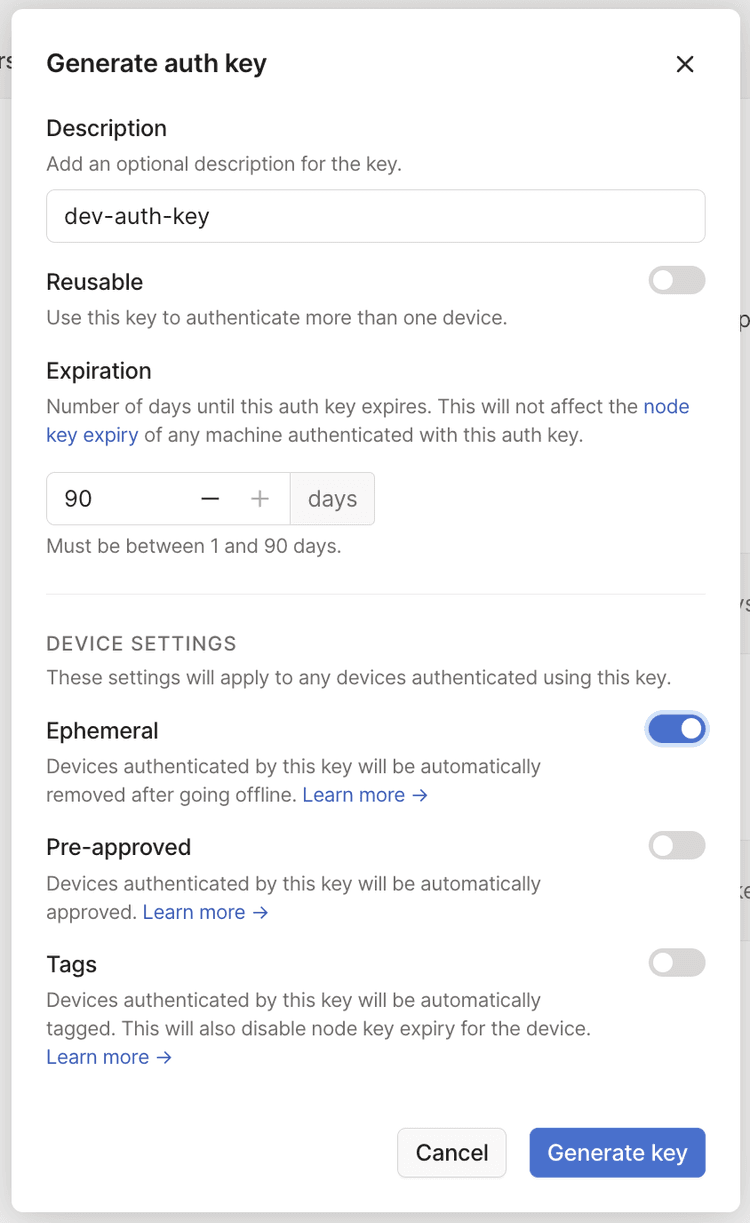
Be careful with auth keys! These can be very dangerous if stolen. They're best kept in a key vault product specially designed for the purpose.
The Pre-approved option will only display in the dialog if device approval is enabled in your Tailscale network.
Step 2: Configure your infrastructure to use the key
The simplest way to do this is to update your usual scripts to use the new auth key:
sudo tailscale up --auth-key=<your ephemeral key>
Instructions vary by platform. See our guides on setting up common platforms:
- Tailscale on Heroku
- Tailscale on Google Cloud Run
- Tailscale on GitHub Actions
- Tailscale on AWS Lambda
- Tailscale on Kubernetes
Step 3: Trigger a build
The next time your infrastructure spins up a new device, you'll see it appear in your admin console as an ephemeral node. It will be able to connect to your network, and will be auto-removed shortly after going offline.
FAQ
Can an ephemeral device remove itself from my tailnet?
Yes. Run the tailscale logout command on an ephemeral device to remove it from your tailnet
immediately. For example, you can add tailscale logout as a last step in your ephemeral node deployment script to immediately remove it from your tailnet
when the script completes.
Another way is if you created an ephemeral device by running tailscaled with the --state=mem: flag. If the device is running Tailscale v1.30
or later, when the device exits, the tailscaled daemon itself performs tailscale logout which immediately removes the device from your tailnet.
How long before ephemeral devices are auto-removed?
Ephemeral devices are auto-removed anywhere from 30 minutes to 48 hours after the last activity. This timeframe is subject to change as we learn more about what works best for Tailscale users. If you want to remove an ephemeral device immediately, run tailscale logout as described above.
Can I create an ephemeral node without an auth key?
Yes, running Tailscale v1.22 or later. You can run tailscaled with the --state=mem: flag. tailscaled is the
Tailscale daemon that runs on devices that have installed the Tailscale client. The --state=mem: flag registers the
node as an ephemeral node so that the daemon stores state in memory, instead of writing it to disk.
