Use CrowdStrike ZTA scores to restrict device access
CrowdStrike Falcon Zero Trust Assessment calculates a numeric trust score (from 0 to 100) for each device that runs a Falcon agent. Using that score as part of access rules in Tailscale can allow organizations to grant access to sensitive resources only to devices that have a high enough level of trust.
This can be achieved using Tailscale's device posture features:
- CrowdStrike Falcon posture integration, which synchronizes Zero Trust Assessment scores from CrowdStrike to device posture attributes in Tailscale.
- Device Identity Collection, which collects identifiers (for example, serial numbers), used to match devices in Tailscale to devices in CrowdStrike.
- Posture conditions in access rules, which allows configuring access restrictions based on device attributes.
This document provides instructions on how to:
- Enable Device Identity collection for your tailnet.
- Configure CrowdStrike Falcon posture integration.
What is CrowdStrike Falcon posture integration?
CrowdStrike Falcon posture integration lets you connect your Tailscale network to CrowdStrike Falcon. It runs regularly and copies Falcon Zero Trust Assessment scores to device posture attributes.
When configured, it will regularly:
- Fetch a list of hosts recorded in your Falcon account, and their ZTA scores.
- Match Falcon hosts with corresponding devices in your tailnet, based on the serial numbers associated with a device.
- Write the ZTA score of each device into the
falcon:ztaScoreTailscale device posture attribute.
Prerequisites
- Device Identity Collection is enabled, and devices on your tailnet are reporting identifiers
- CrowdStrike Falcon API credentials
Create CrowdStrike Falcon API credentials
Generate a CrowdStrike Falcon API client that will be used to fetch a list of hosts from Falcon along with their ZTA scores.
-
In Falcon, open Support and resources and then API clients and keys.
-
Click Create API client.
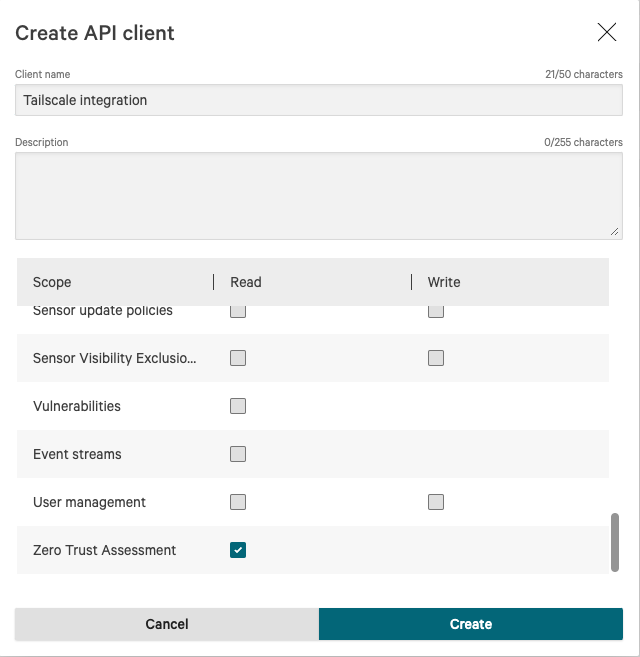
-
Add a name. For the Hosts scope add Read, and for the Zero Trust scope add Read.
-
Click Create, then make sure to copy the displayed Client ID and Client Secret. These will be only displayed once.
Also make a note of the Base URL (for example, https://api.us-2.crowdstrike.com).
Configure CrowdStrike Falcon posture integration
Configure Tailscale to fetch the ZTA scores from CrowdStrike Falcon.
-
Open the Device management page of the Tailscale admin console.
-
Under the Device Posture section, click Connect next to the CrowdStrike Falcon integration.
-
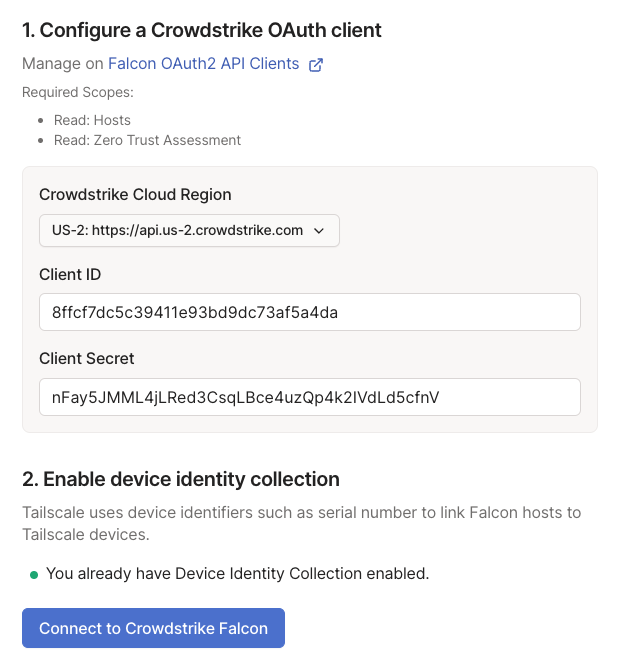
Select your CrowdStrike Cloud Region (the Base URL from the API client).
-
Enter your Client ID and Client Secret.
-
Click the Connect to CrowdStrike Falcon button.
View the integration status
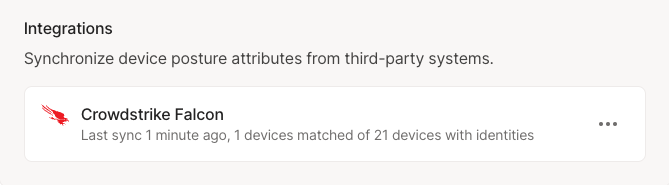
Check that the integration has run successfully.
In the Device Posture section of the Device management page, configured integrations and their status will show under Integrations. The time of the most recent sync will display here. If an error occurs while synchronizing, it will display here.
Check node attributes
After you configure CrowdStrike Falcon posture integration, you can confirm that the Zero Trust Assessment score attribute is being written for your Tailscale nodes via the Machines page of the admin console.
- Open the Machines page of the Tailscale admin console.
- Select a machine you want to inspect.
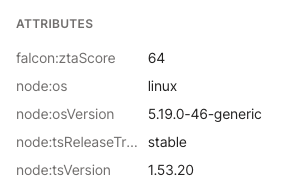
- The attributes for the machine are in the Machine Details section. This should include the
falcon:ztaScoreattribute.
You can also check node attributes via the API.
Adjust Tailscale access rules
Once CrowdStrike Falcon posture integration is configured and your devices have a device posture attribute that reflects their Falcon trust score, you can use that device posture attribute as part of your posture rules.
For example, to only allow access to tag:production from devices that have a CrowdStrike ZTA score of 70 or higher, you can create a new posture and use it as part of a corresponding access rule:
"postures": {
"posture:trusted": ["falcon:ztaScore >= 70"],
},
"acls": [
{
"action": "accept",
"src": ["autogroup:member"],
"srcPosture": ["posture:trusted"],
"dst": ["tag:production:*"],
},
]