Winter Update Week 2026
Built for momentum
Secure connectivity makes things easier to run, easier to think through, and harder to mess up, even as environments get more dynamic.
Fast, centralized AI access designed for security
Identity-aware AI usage without API key sprawl.
Aperture by Tailscale (open alpha)
Aperture provides visibility and control over AI agent usage by centralizing access and tying it to Tailscale identity. It acts as an AI gateway that eliminates the need to distribute API keys to devices and agents, leverages Tailscale identities to associate usage with users and machines, works with common coding agents and LLMs without blocking developer workflows, and centralizes usage logs for adoption insights, cost analysis, and compliance.
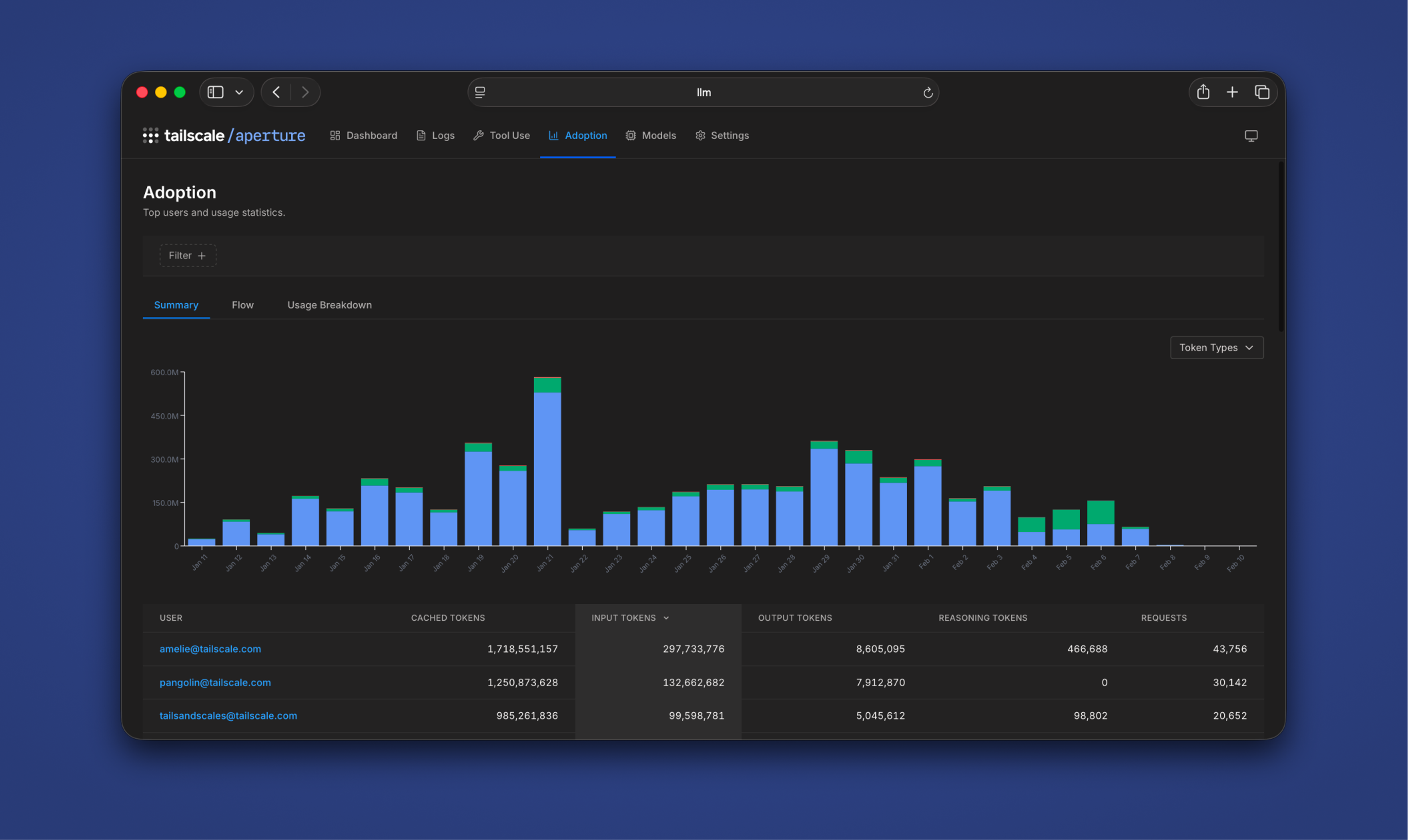
High performance across real-world networks
High-throughput connectivity for constrained environments with improved logging and device posture enforcement.
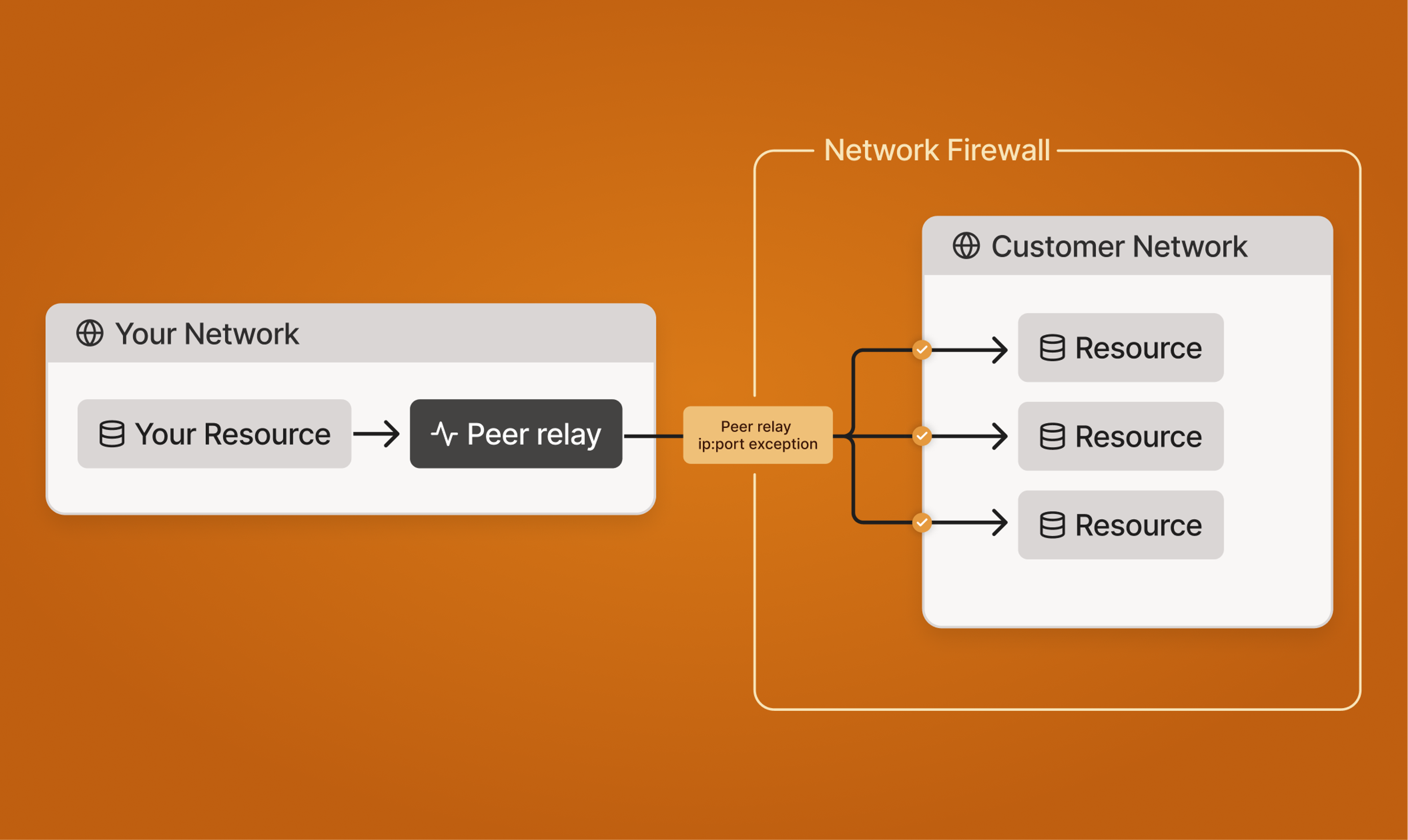
Tailscale Peer Relays (GA)
Tailscale Peer Relays now delivers significant throughput and reliability improvements at scale through customer-deployed, managed relays. Peer Relays ensures strong performance even in restrictive environments with smarter relay selection, support for static endpoints behind firewalls and load balancers, and the ability to replace traditional subnet routers while preserving Tailscale features.
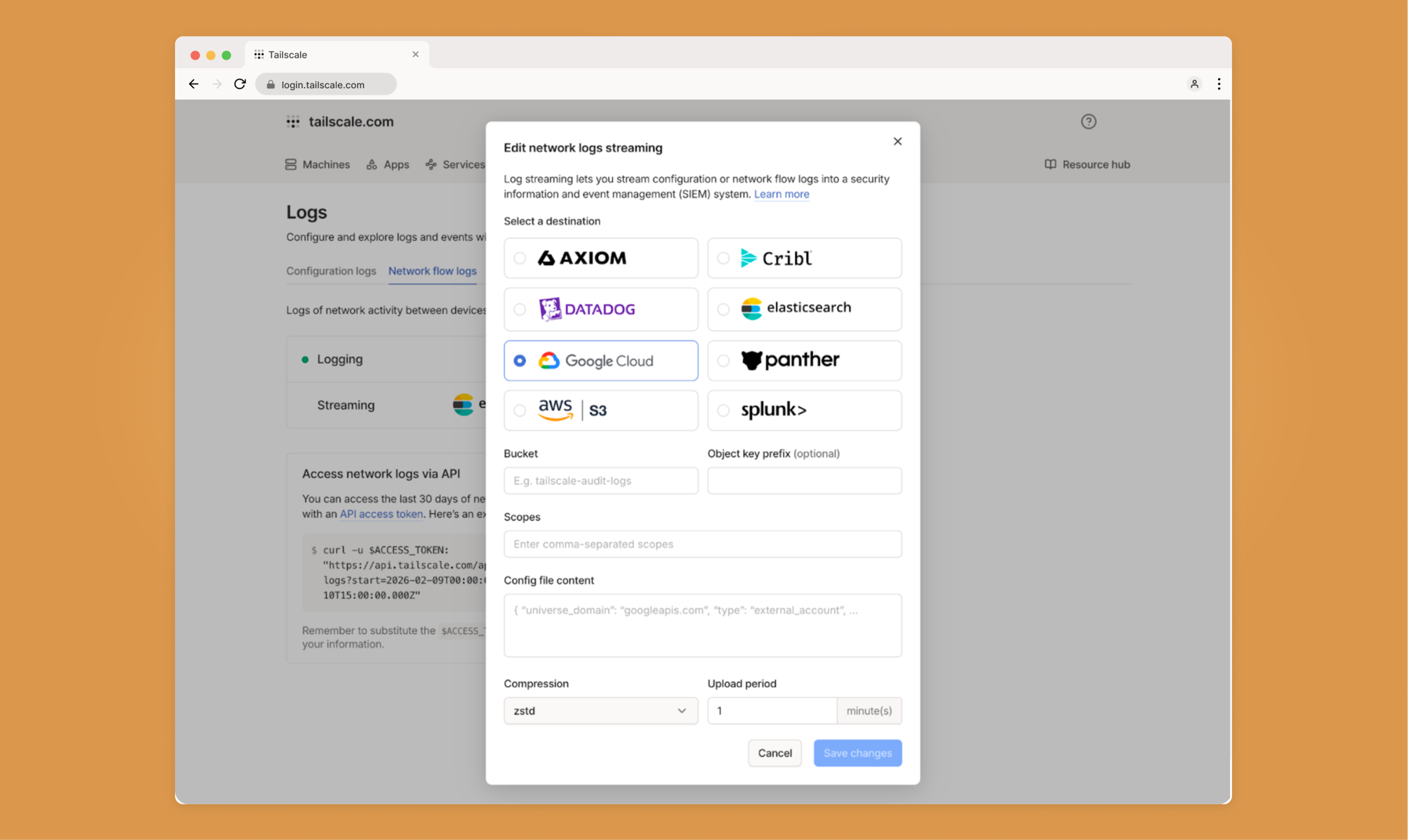
GCS log streaming
We’ve extended log streaming support to Google Cloud Storage (GCS) so you can stream network flow and audit logs to a customer-owned GCS bucket. GCS log streaming enables end-to-end encryption while maintaining visibility and allows you to apply existing GCP IAM controls, retention policies, and downstream workflows.
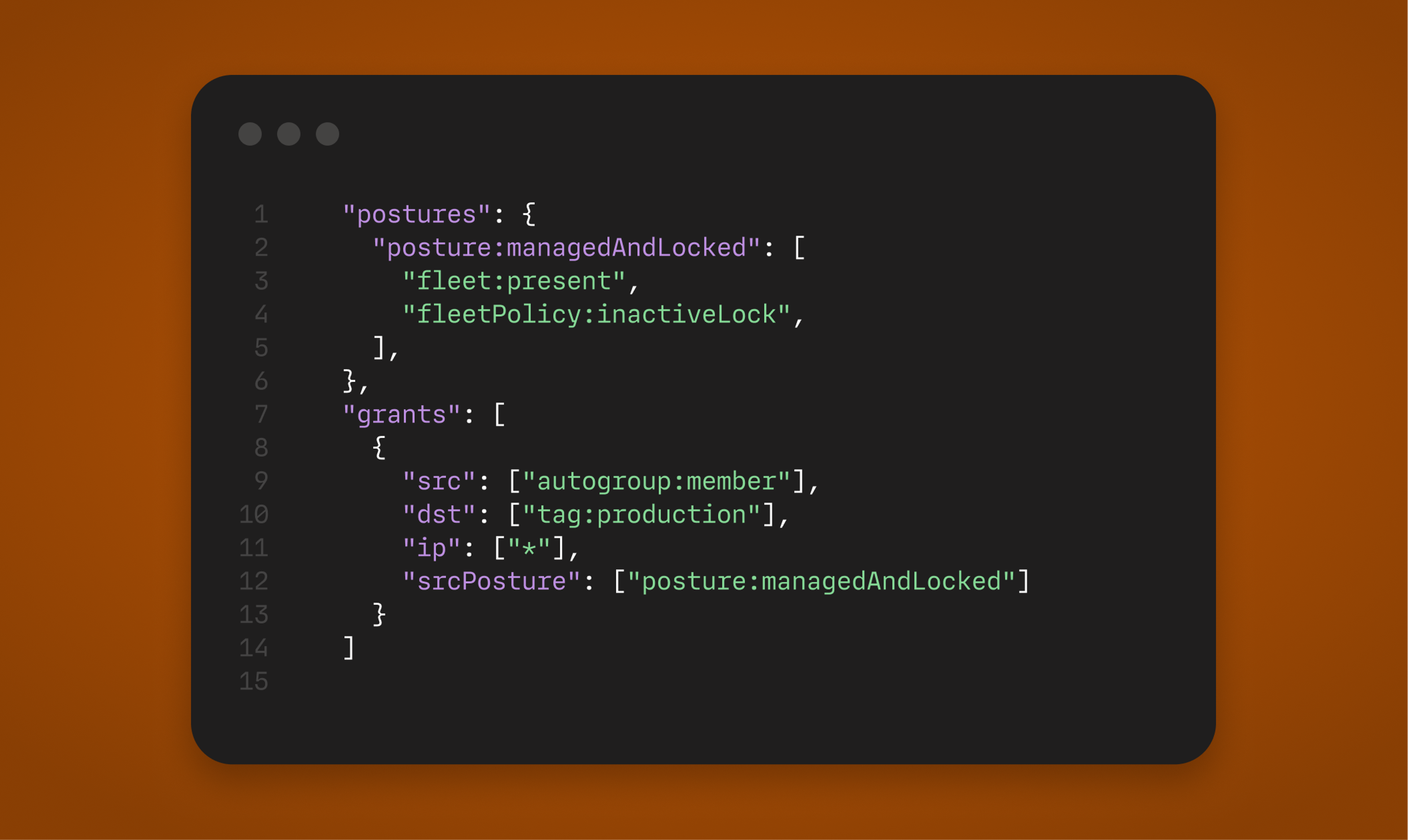
Fleet device posture integration
The new Fleet device posture integration connects device management and access enforcement. Fleet enrollment and policy state can be used in access rules to ensure only actively managed devices are granted access. When a device falls out of management or no longer meets defined conditions, enforcement reflects that change automatically.
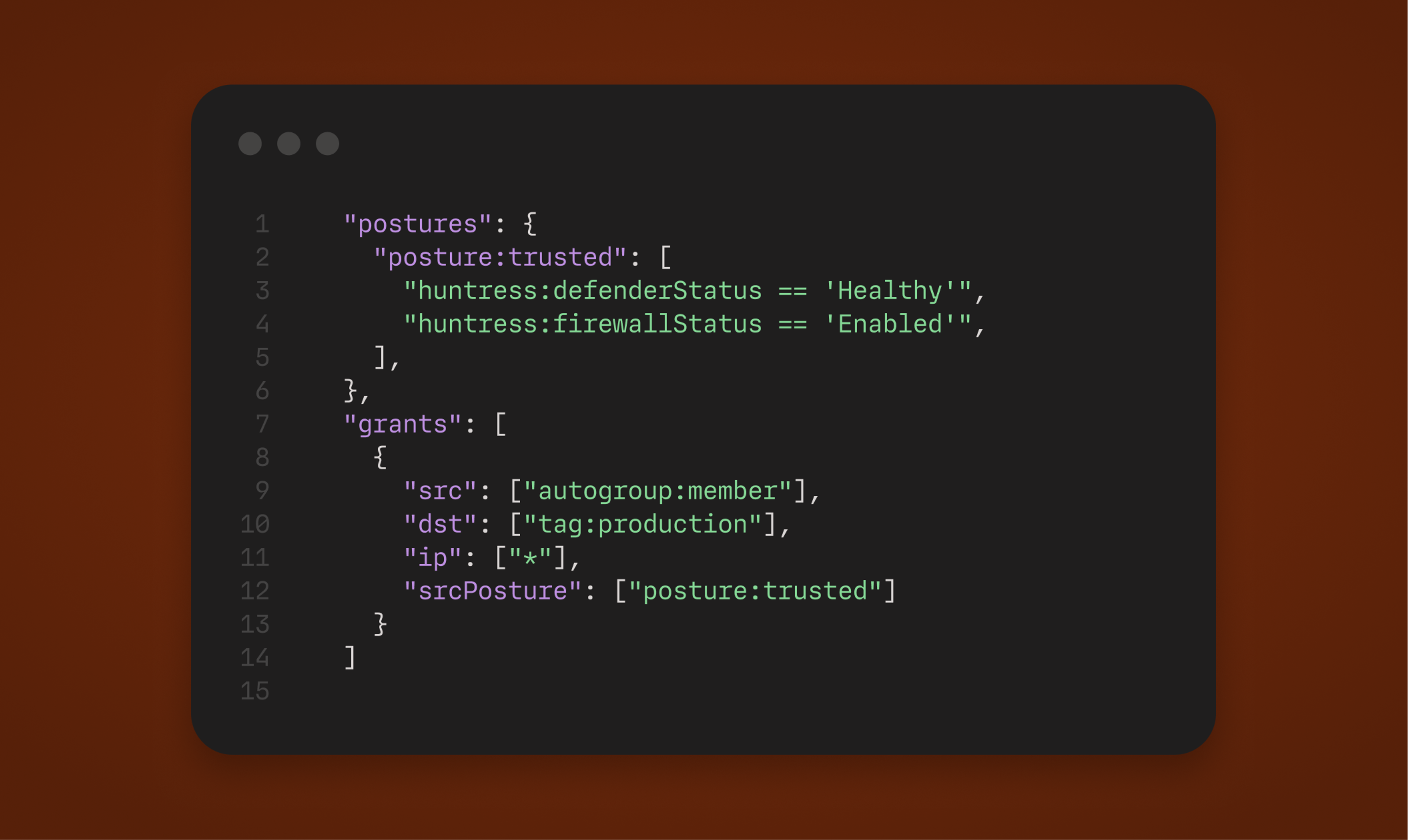
Huntress device posture integration
Our Huntress device posture integration incorporates endpoint protection status into access enforcement. Antivirus and firewall state can be used in access rules to require baseline protections before devices reach critical systems. As protection status changes, enforcement stays aligned without manual updates.
Service connectivity with greater control
Application-aware service connectivity across environments, secured with keyless workload identity.
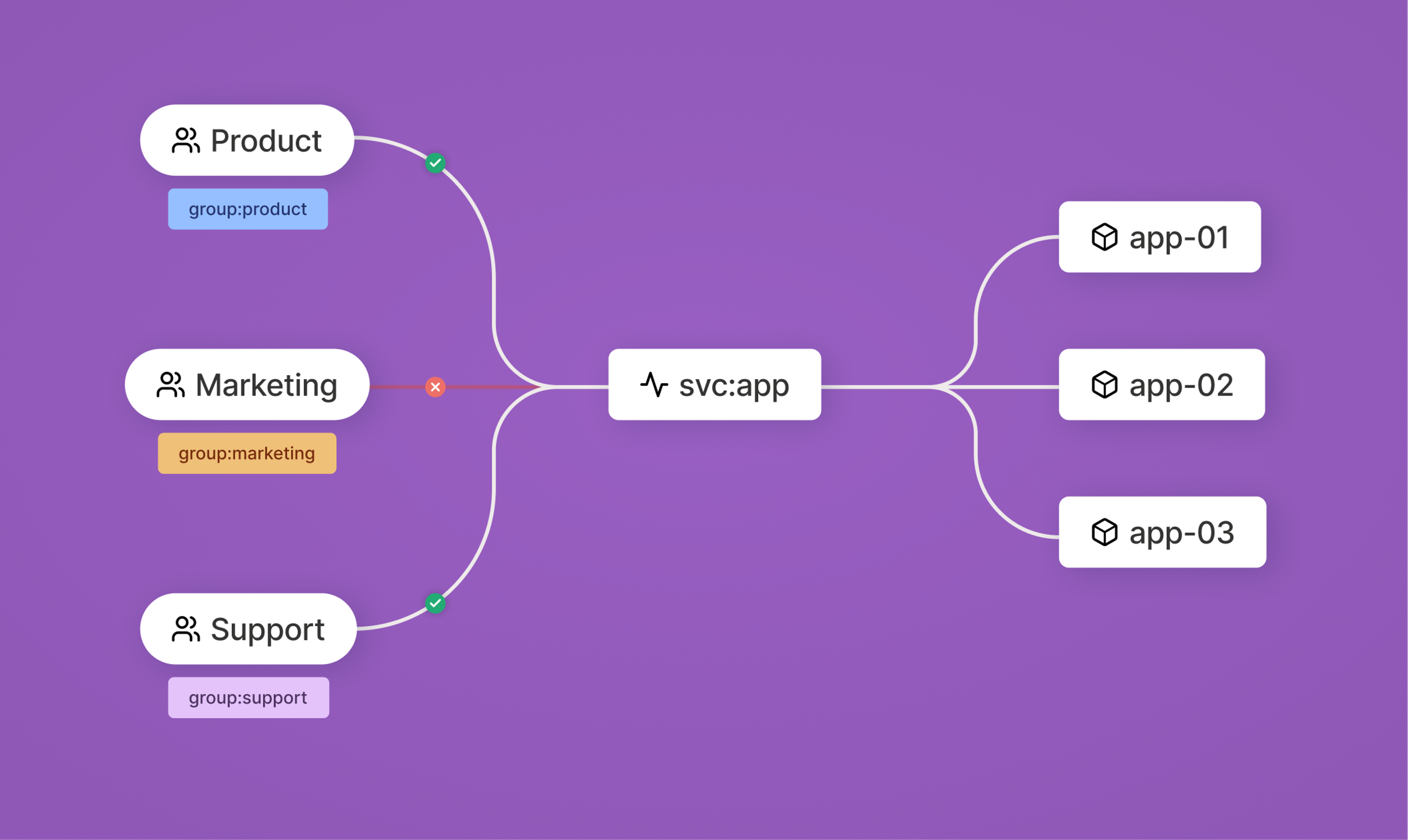
Tailscale Services (GA)
Tailscale Services now integrates with tsnet applications to automatically register, route, and drain traffic based on application lifecycle events, simplifying service connectivity. It also provides service proxies for remote destinations, such as managed databases, third-party APIs, or services behind a subnet router. Declarative JSON configuration enables GitOps-style workflows, while per-service audit and flow logs and built-in access control testing provide strong observability and policy validation before deployment.
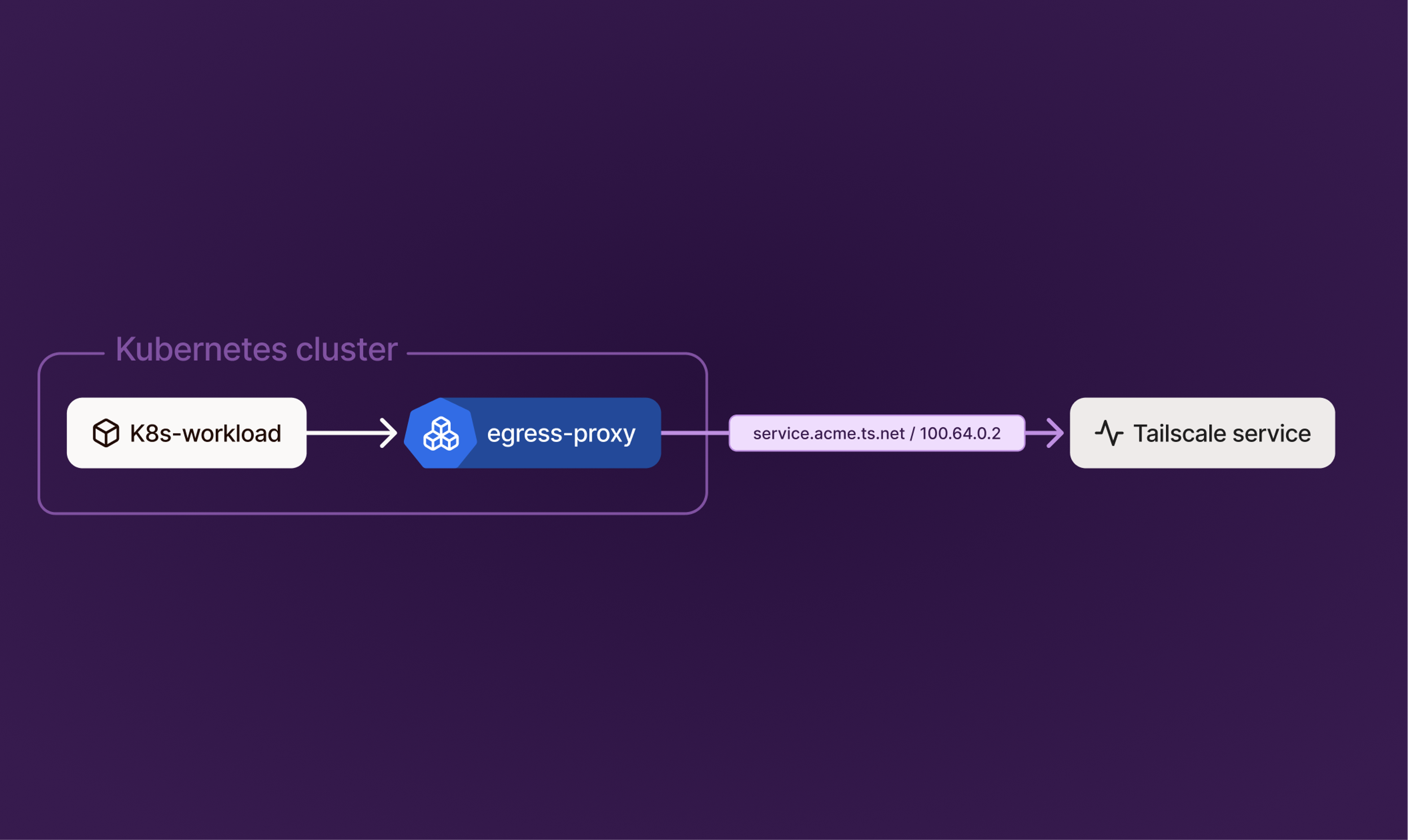
Kubernetes egress proxy for Tailscale Services
The Tailscale Kubernetes Operator’s egress proxy is now aware of Tailscale Services, allowing workloads running inside Kubernetes pods to initiate outbound connections to any Service published in a tailnet. With this capability, Kubernetes applications can egress to Services regardless of where they’re running, whether on another cluster, a VM, or an external environment, using the same service-aware connectivity model.
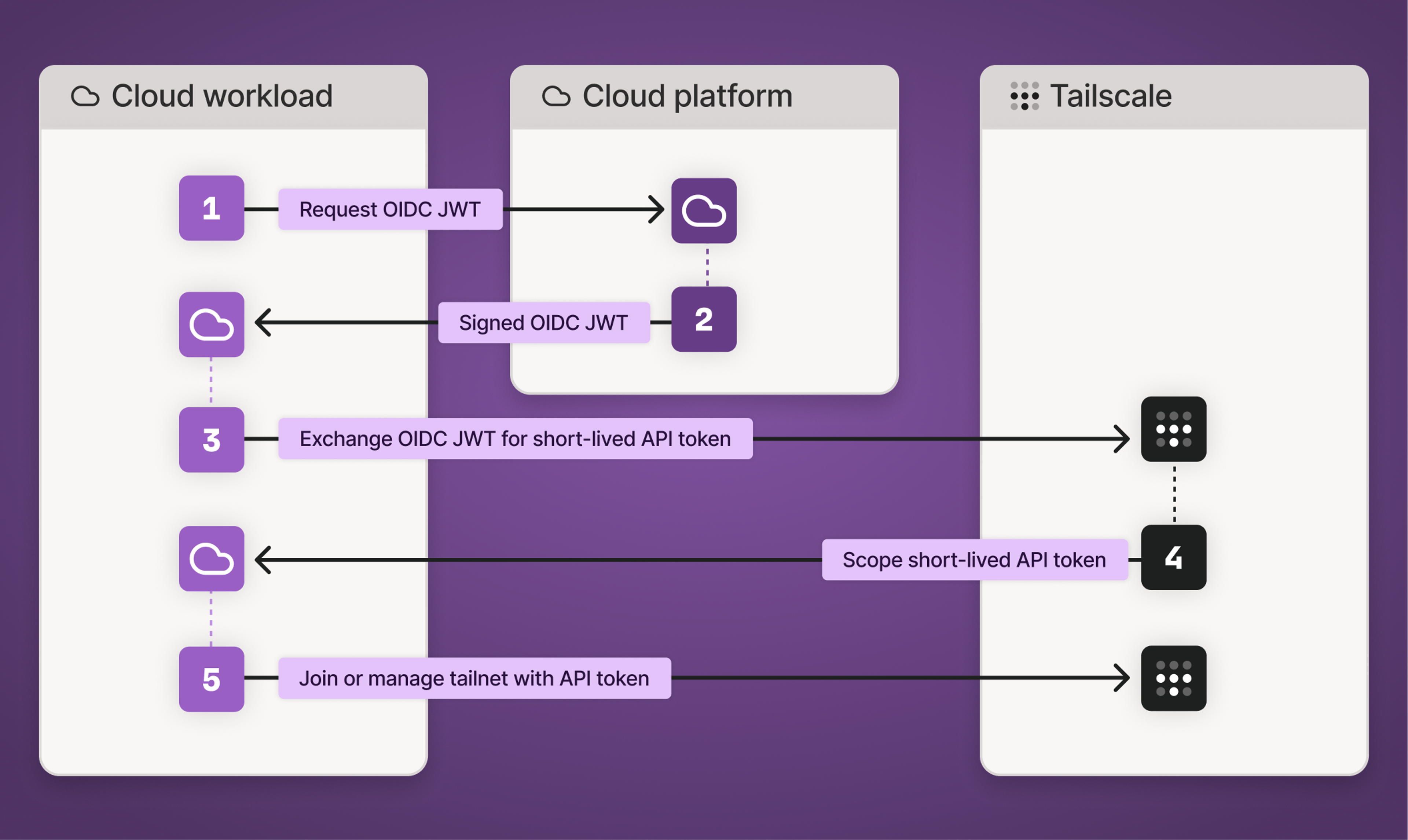
Workload identity federation (GA)
Federated identities can be created and managed through the Tailscale API and Terraform provider, allowing teams to define and maintain trust relationships as code and eliminating static API keys. Applications can authenticate without embedded secrets, while automatic cloud token discovery and exchange supports AWS, GCP, and GitHub environments.
Visible and auditable privileged access
Identity-aware auditing across Kubernetes workloads, network flow logs, and SSH access in Linux.
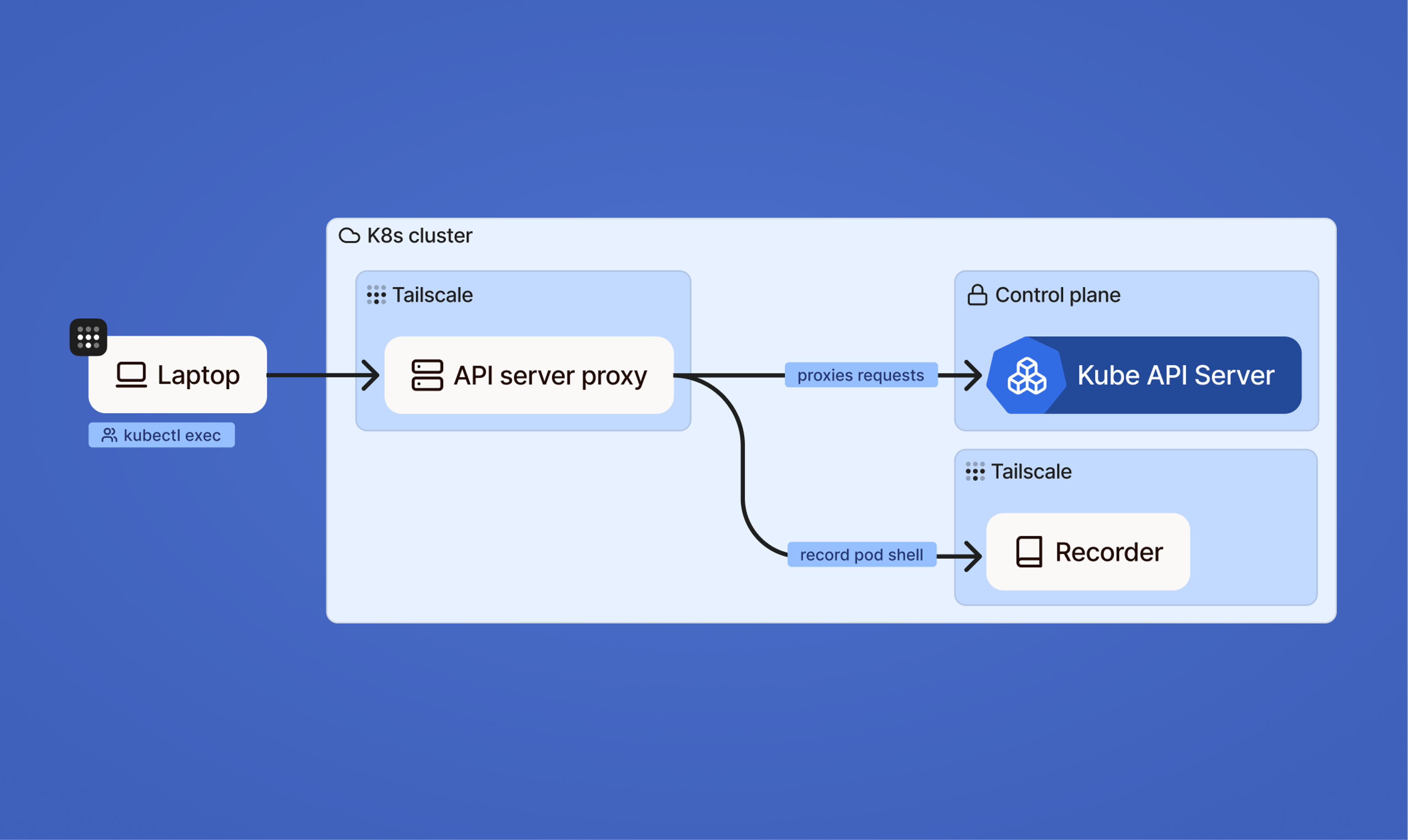
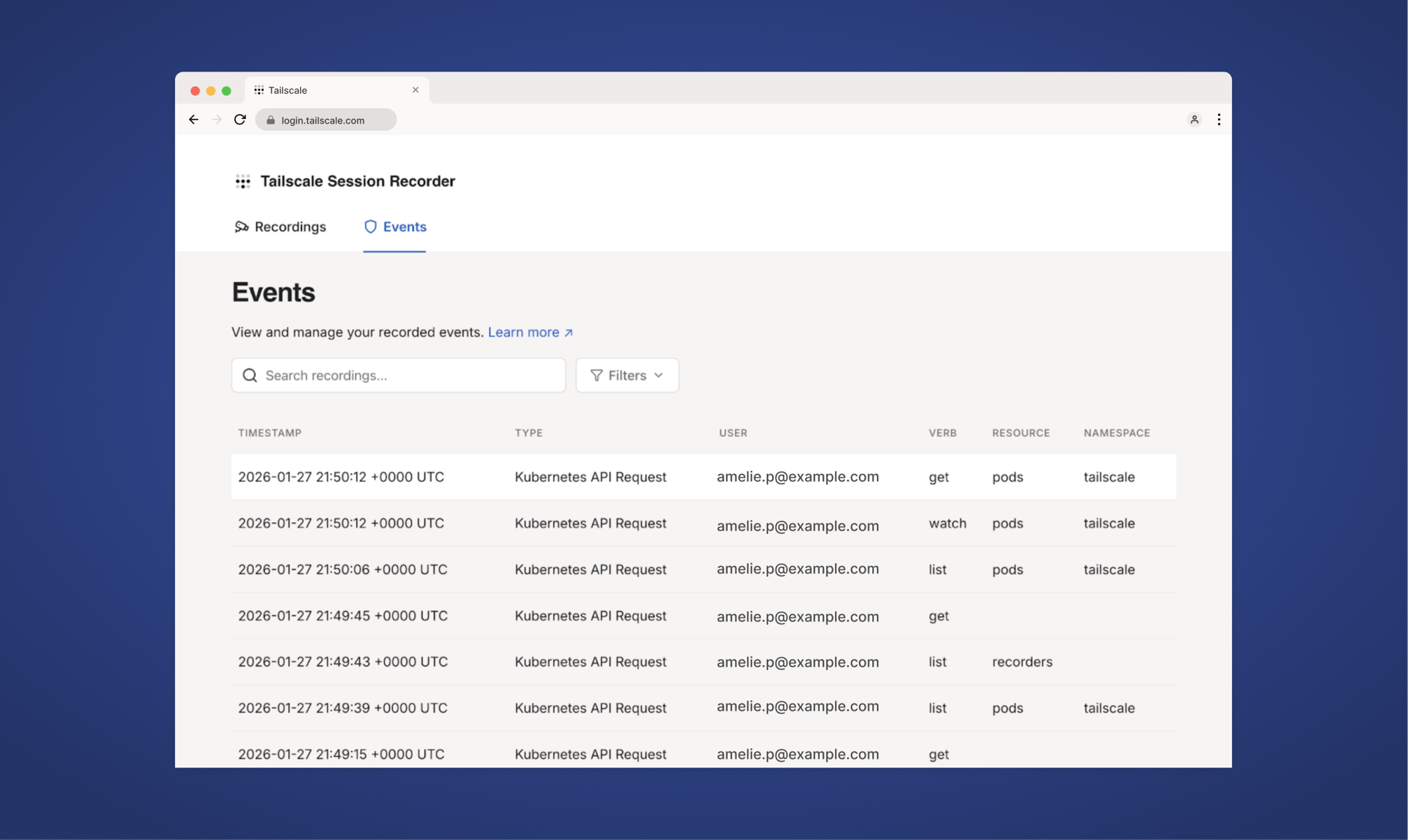
Kubernetes API proxy audit logging (beta)
Tailscale records individual Kubernetes API requests at the moment they are received and emits them as structured audit logs. Now in beta, this captures individual HTTP requests made to the Kubernetes API and exports audit data to cold storage, supporting long-term retention and compliance requirements. Structured logs make querying, searching, and forensic analysis easier, and you now have just one platform for connectivity, access control, and Kubernetes auditing.
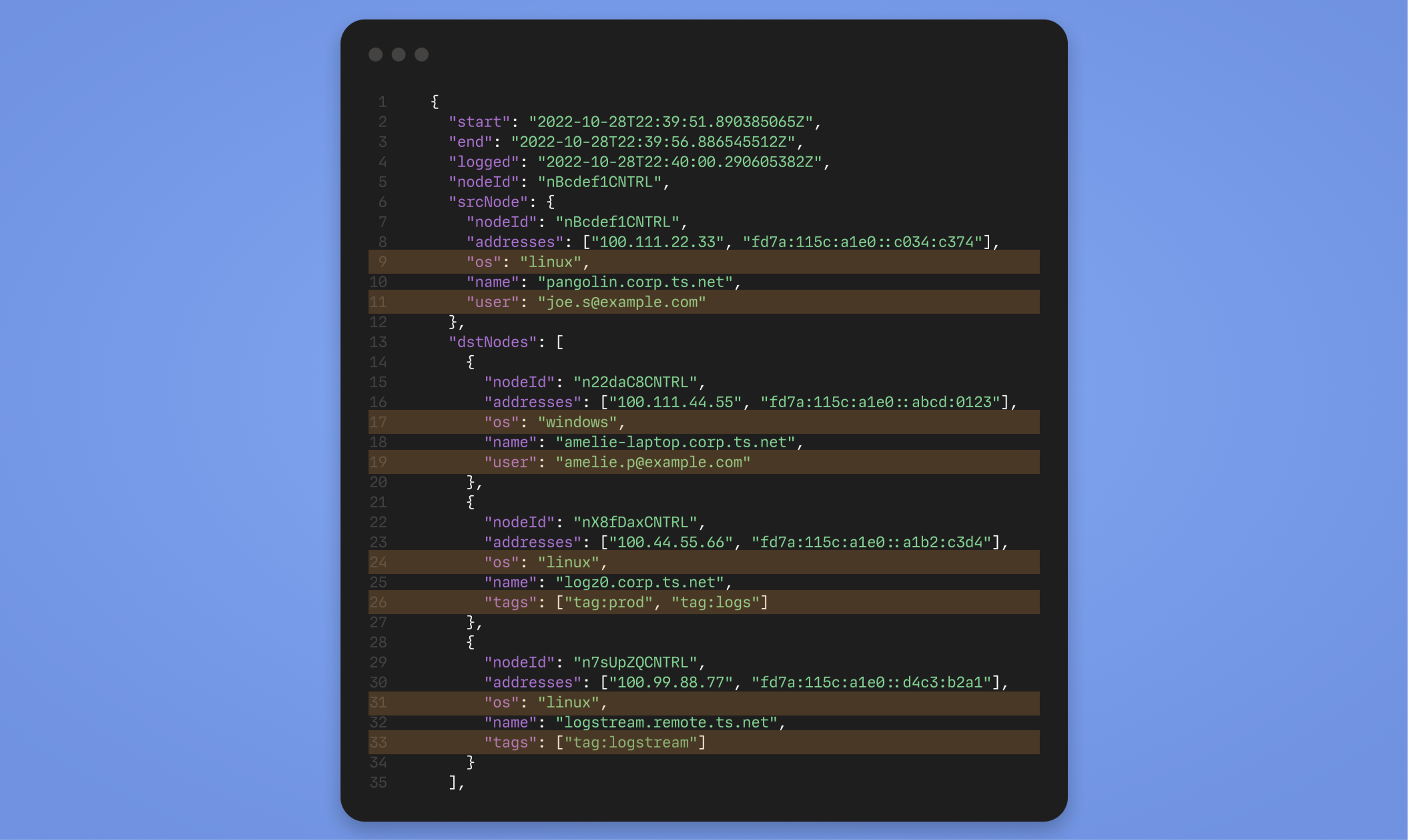
Actor identifiers in network flow logs
Enrich network flow logs with actor context, including user identity, device identity, and human-readable device names. This means that identity context is built directly into network flow logs, turning raw network data into meaningful access records and eliminating the need for separate log enrichment pipelines.
SSH logins in Linux
Bridge the gap between identity-based access and host-level auditing without changing how teams already operate their systems with SSH logins in Linux. This works with native Linux audit systems (auditd, journald, kauditd), covers both Tailscale SSH and traditional SSH, and reduces audit ambiguity without added agents or tooling.
Ready to dive in?
Your tailnet is about to get so much better.
Tailscale Peer Relays
High-throughput connectivity for networks even in constrained environments.
Kubernetes egress proxy for Tailscale Services
Service-aware connectivity from inside Kubernetes.






