Tailscale SSH
SSH access without the infrastructure overhead
Manage SSH access across environments with zero-touch configuration and granular team controls. Trusted by DevOps and platform teams.

Simplify SSH key management
Automate key creation, rotation, and expiration — no scripts, no spreadsheets, and no manual effort.
Access infra from any device
Deploy SSH from any device and across operating systems. Answer an on-call emergency from anywhere.
Integrates with your identity stack
Enforce SSO and MFA with Okta, Google Workspace, or any SAML IdP. Every session is tied to the right user.
Trusted by 10,000+ global companies
Improve security with automated SSH management
Stay secure while saving time
Easily manage shell access to any Linux-based infrastructure and reduce the risk of mismanagement that comes with static SSH keys and manual sharing and rotation. Verify user identities against existing identity providers (e.g. Google Workspace or Okta) and manage access via centralized ACLs.


Get quick, compliant authentication
Enable session recordings for audits and instantly revocable access via ACLs. Keep your existing identity provider and multi- factor authentication to protect SSH connections.
Stay secure by default
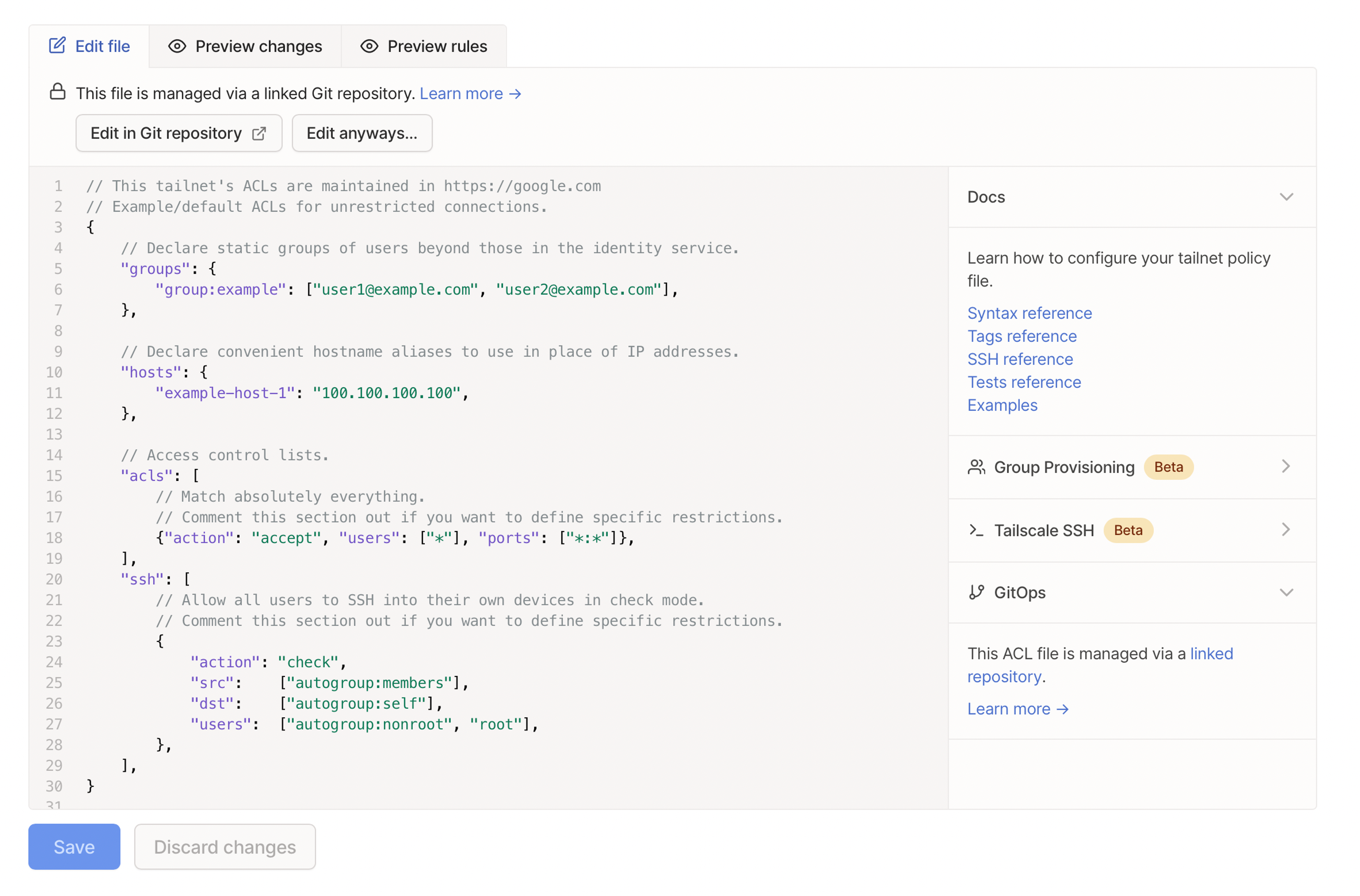
Define access instead of reusing keys
Use SSH keys that are unique to each network to ensure keys aren't reused. Define what connections you’ll allow using a standard syntax in a centralized configuration file.
Access public servers safely
Stay protected with secure, end-to-end encryption that’s powered by WireGuard protocol.
Reduce latency and exposure
Connect directly from your device to your server without a bastion for lower latency and one less point of exposure.
Rotate keys effortlessly
Manage key distribution and rotation with a single command. Each server and user device has its own node key.
The power of Tailscale SSH in your browser
Tailscale SSH console
SSH from your browser to devices on your Tailscale network from anywhere you can access the Tailscale admin console.
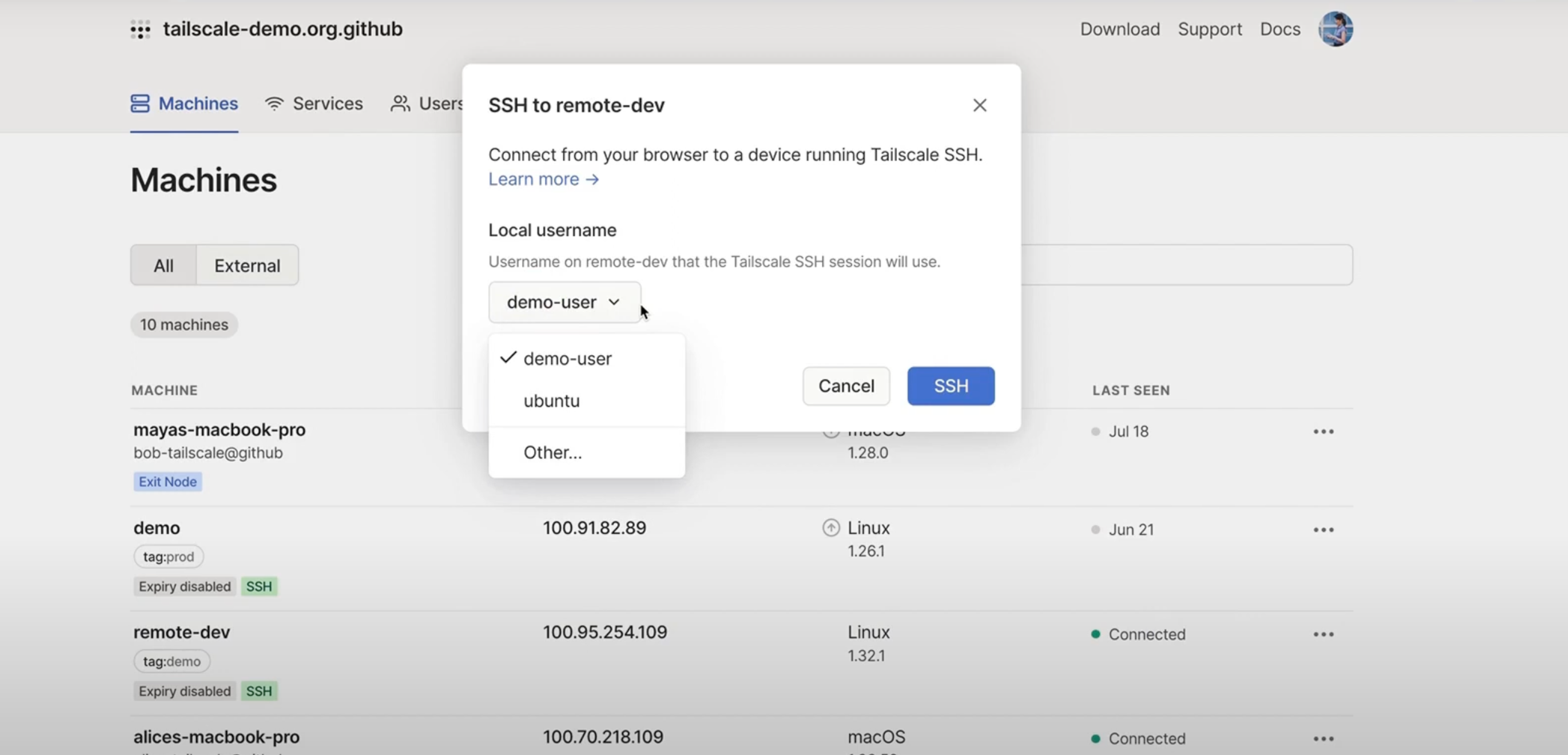
Protected by SSO and MFA
Initiate a secure browser-based SSH session from any device, even without Tailscale installed on that device.
Respond quickly to any emergency
As long as you can access your admin console, you can initiate an SSH session in seconds.
Automatically terminate sessions
These connections automatically end when the browser window closes, without the need to clean up SSH keys.
Pricing that works for everyone
For individuals who want to securely connect personal devices, for free.
For small teams seeking an easy-to-use and quick-to-deploy secure network access solution.
For growing teams seeking advanced service/resource-level networking and identity-aware access controls.
For organizations seeking advanced user and posture management, robust compliance, and dedicated support.
FAQ
Read our frequently asked questions or talk to a Tailscale team member to learn more. Over 9,000 Engineering and IT teams use Tailscale’s networking software to secure their work from anywhere, reduce developer disruption, and protect infrastructure.
