How to secure Remote Desktop Protocol (RDP)
Remote Desktop Protocol (RDP) enables seamless remote access to Windows devices, but its security risks are significant.
What is Remote Desktop Protocol?
Remote Desktop Protocol (RDP) is a type of remote access software that allows remote access to Windows devices. It transmits output from the remote server to the client device, and input from the client device to the remote server.
Put simply, it allows you to see the monitor of the remote machine on your own monitor and to use your mouse and keyboard to interact with the remote machine.
The use of RDP has never been more common than it is now, as platforms such as Hyper-VMicrosoft Azure use it as their default remote connection protocol. With RDP, a remote machine can be used as smoothly and simply as a local one.
Connected resources, automated SSH management
Benefits of RDP
There are any number of reasons why you might want to use RDP to remotely access individual computers or a network. For example, RDP gives technical support providers and other help desk services an easy way to access a remote user’s machine. It also allows remote users to access the same resources they could if they were in the office.
Using RDP provides a number of other benefits that increase efficiency and enhance security, including:
- Remote file sharing: With RDP, the need for traditional data transfer methods, such as USB or cloud drives, is eliminated. Your data stays in one place, and it remains accessible to anyone who would normally have access to it — without requiring any additional software.
Secure a Windows RDP server
- More control: RDP allows you to have control over who can access what. You can specify users’ permissions, restricting their access to sensitive or unauthorized resources. RDP also allows for the management of the network in real time from a remote location.
- Increased efficiency: RDP allows the efficient setup of remote working mechanisms. Once remote access is enabled on the remote device and you’ve configured your network appropriately, the device will remain accessible to your team, regardless of the team’s location.
Drawbacks of RDP
According to CyberArk, more than 4.5 million RDP servers are exposed to the internet. This highlights how often RDP security is overlooked or misconfigured, making those devices easy targets for cybercriminals and other malicious actors.
Remote Desktop Protocol is one of the most commonly exposed services on the internet, but its default configuration may expose vulnerabilities:
- Open Ports: RDP uses port 3389 by default, making it a common target for brute-force attacks. Changing it won't secure your setup because threat actors are already scanning every port on every IP address on the public internet. A change only delays the inevitable, it doesn't prevent it.
- Weak Passwords: Poor password practices expose sessions to credential theft. Threat actors often gain access to RDP by exploiting weak passwords or stolen credentials.
- Session Hijacking: Attackers can take over active sessions and gain unauthorized access to sensitive resources.
- DDoS Attacks: RDP servers can be overwhelmed by traffic, rendering them inaccessible.
- Unpatched Systems: Exploits such as BlueKeep highlight the risks of unpatched vulnerabilities in RDP servers. Securing remote desktop services through regular updates and strong authentication measures is crucial.
Strategies to secure RDP
Securing the remote desktop session host and enhancing security for remote desktop connections will prevent unauthorized access and data breaches.
However, the best way to secure your servers is to not expose them to the public internet at all, and instead expose RDP only over Tailscale.
Here are six other secure RDP strategies for organizations:
Strengthen Network Level Authentication
- Require complex passwords with a minimum of 16 characters, mixing upper- and lowercase letters, numbers, and symbols.
- Use multi-factor authentication (MFA) to add an additional security layer, such as one-time passcodes or biometric verification.
Restrict Access
- Configure firewalls to allow RDP connections only from specific IP ranges.
- Limit RDP access to users who require it and ensure permissions align with their roles.
- Disable local administrator accounts from using RDP to reduce exposure.
Encrypt Connections
- Enable Network Level Authentication (NLA) to authenticate users before establishing an RDP session.
- Use encryption protocols such as TLS to secure data transmission.
Regular Updates and Patching
- Apply security updates for both RDP clients and host systems.
- Monitor advisories for newly discovered vulnerabilities and act promptly to mitigate risks.
Leverage VPNs for Secure Access
- Deploy a virtual private network (VPN) to create an encrypted tunnel between remote users and the corporate network.
- Combine VPN and RDP to add a layer of security by hiding RDP endpoints from external threats.
Implement Lockout Policies
- Configure lockout policies to block accounts after multiple failed login attempts.
- Monitor account activity to detect brute-force attacks or unusual access patterns.
Tools and Solutions
To ensure the security of RDP connections, several tools and solutions can be implemented:
- Virtual Private Network (VPN): A VPN creates a secure, encrypted tunnel between the user’s computer and the remote computer, protecting RDP connections from interception and eavesdropping.
- This additional layer of security helps hide RDP endpoints from potential attackers.
- Multi-Factor Authentication (MFA): MFA requires users to provide additional forms of verification, such as a smart card or biometric data, to access the remote computer.
- This significantly reduces the risk of unauthorized access by adding an extra layer of security beyond just passwords.
- Network Level Authentication (NLA): NLA requires users to authenticate with the remote computer before establishing an RDP session, adding an extra layer of security.
- This ensures that only authenticated users can initiate an RDP session, reducing the risk of unauthorized access.
- RDP Gateway: An RDP Gateway acts as a middleman between the user’s computer and the remote computer, managing and securing RDP traffic.
- This provides a centralized point for managing RDP connections and can enforce security policies.
- Secure RDP Clients: Secure RDP clients, such as those that use SSL/TLS encryption, can provide an additional layer of security for RDP connections.
- These clients ensure that the data transmitted during the RDP session is encrypted and secure.
Implementing these tools and solutions can significantly enhance the security of RDP connections, protecting against various threats and vulnerabilities.
Alternatives to RDP
RDP is not the only solution for remote access. Depending on organizational needs, these alternatives may offer additional features or security:
- SSH (Secure Shell): SSH is ideal for managing Linux systems with command-line access.
- Third-Party Remote Access Tools: Solutions like TeamViewer or AnyDesk provide additional features such as screen sharing and session recording.
- Zero Trust Network Access (ZTNA): A modern approach that restricts access to specific applications and resources, zero trust minimizes the attack surface.
When RDP Makes Sense
RDP makes sense for many organizations, especially when used as a tool for:
- IT teams managing multiple servers or workstations in distributed environments.
- Remote employees accessing centralized applications and files.
- Organizations requiring cost-effective and scalable remote access solutions.
Using Tailscale for secure RDP
An easy way to achieve network configuration is with a VPN like Tailscale, which allows you to make your RDP host accessible outside of the local network, improving encryption and authentication capabilities.
Encryption
By default, RDP uses Transport Layer Security (TLS, the same thing that HTTPS and your bank use) for encryption.
Making RDP accessible over Tailscale obviates the need to care too much about which encryption method is used. Once the RDP session runs over Tailscale, RDP’s own security is augmented by Tailscale’s use of WireGuard, an end-to-end encrypted tunnel.
This adds a second level of end-to-end encryption that can additionally protect your most private information from threat actors.
Network Level Authentication
If you’re working in a managed enterprise environment where both the client and the target server are managed by the same Active Directory instance, you can also use Network Level Authentication (NLA). This adds an additional layer of security to the process by requiring strong authentication using Credential Security Support Provider before the connection will be established. NLA also reduces the chances of man-in-the-middle attacks. Please note that this will only apply in managed enterprise networks. Enabling this on non-enterprise installs of Windows has a very high likelihood of breaking everything related to RDP authentication.
With Tailscale, you can enable Network Level Authentication using the following steps:
- Open Control Panel and navigate to System.
- Click on Advanced settings under the Enable Remote Desktop.
- Enable the check of Configure Network Level Authentication.
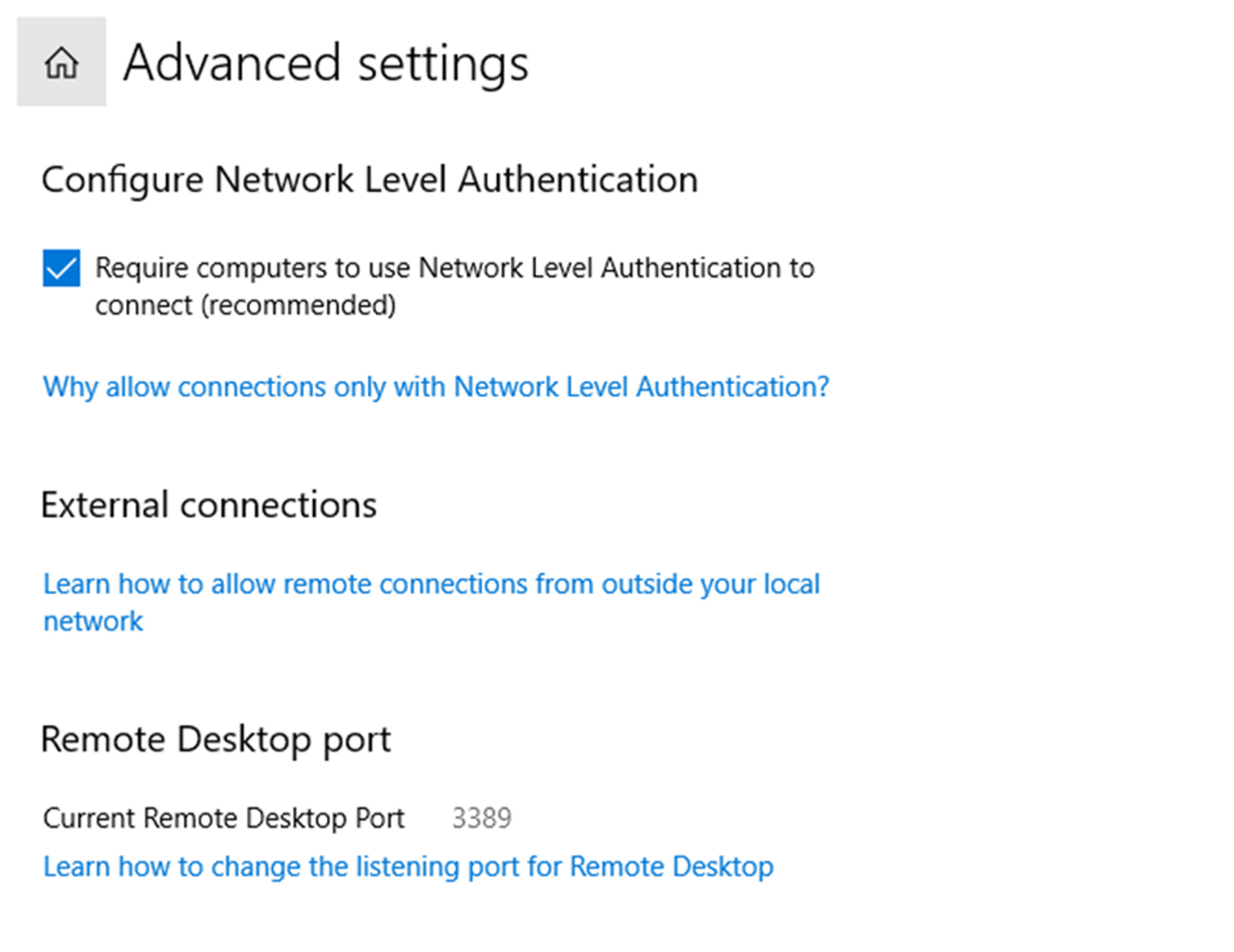
That’s all that it takes to enable Network Level Authentication, significantly improving the security of your remote desktop services.
Watch this video to understand how Tailscale works, then download Tailscale to start using it for free.
FAQs
What are the consequences of not securing RDP?
The consequences of not securing RDP can be devastating. If someone exploits a vulnerability or brute-forces a password, they’ll have access to your entire system. RDP exploits are common vectors for data theft, malware, and ransomware.
How can I make RDP less risky?
There are several steps you can take to increase the security of RDP, including enabling encryption and Network Level Authentication.
Are there better security options?
The safest way to use RDP is to avoid exposing it to the internet at all. This can be done by using it exclusively on local networks, or by setting it up as part of a VPN like Tailscale.






