Secure remote access
Remote access without the headaches
Let your team securely reach dev, staging, and prod from anywhere, without managing a VPN.

Trusted by 10,000+ global companies
Connect your resources
Secure connections across every user, machine, container, VM, bare metal, and Kubernetes cluster—anywhere. Automate critical infrastructure access.
Automate SSH management
Streamline development with the power to SSH to any device without extra bastions. Avoid more hardware to manage, public IPs, and high latency.
Adopt a modern Business VPN
Deploy an advanced Business VPN that’s zero-trust ready. Gain fine-grained access control, device posture checks, just-in-time access, and more.
Reduce access complexity
Promote uniform SSH access
Create one secure, shared network to SSH into resources across Google’s GCP, Amazon’s AWS, Microsoft’s Azure, on-prem, and hybrid. Tailscale is compatible with any environment and OS including Windows, Mac, Linux, and more.
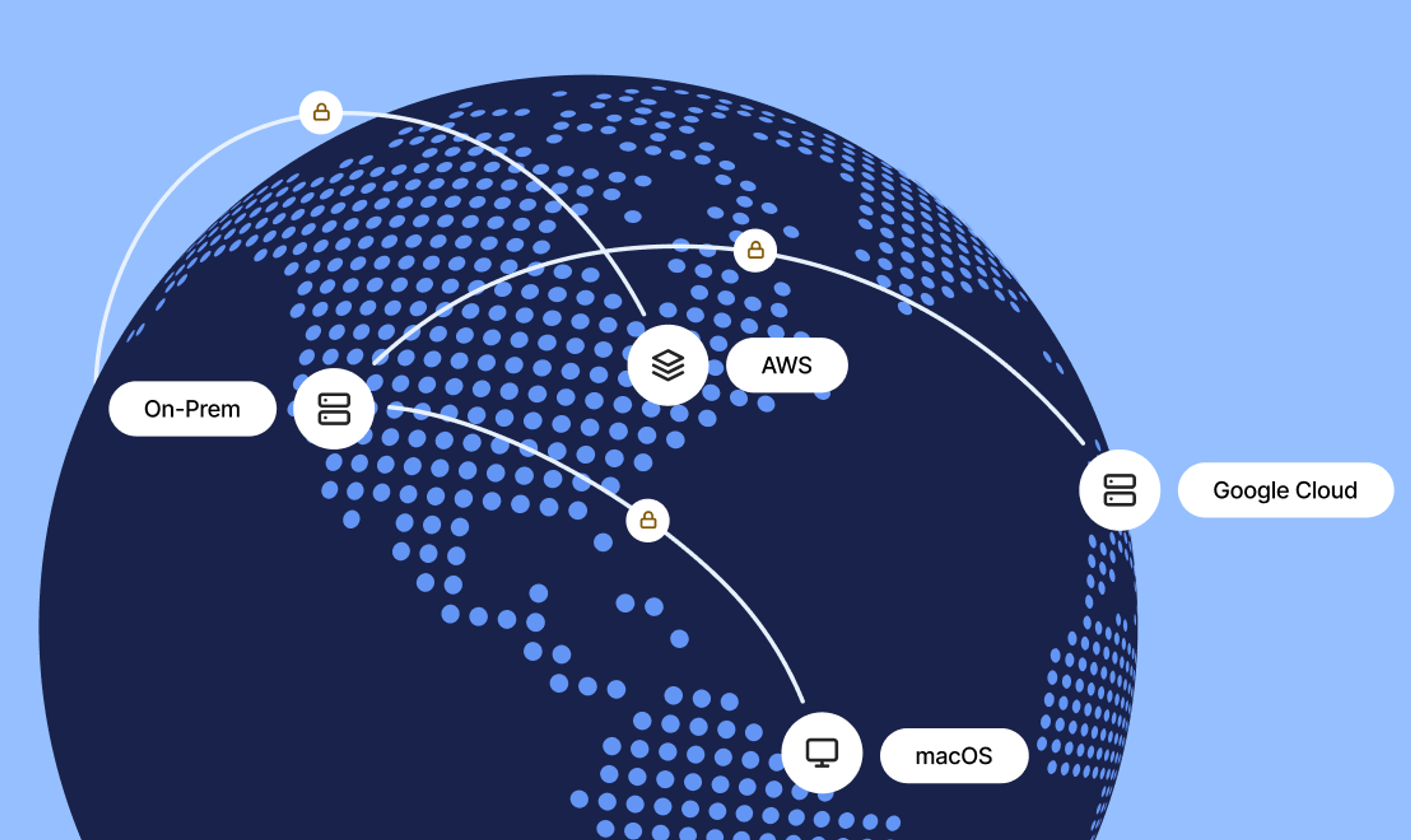

Enjoy secure networking for the office or the road
Experience better collaboration across every user and machine, anywhere. Toss out VPN gateways and bastion hosts for direct connections with better performance. Gain ease of management and flexibility with performant and reliable connections.
Discover secure access built with developers in mind

Gain secure access that developers love
Manage shell access to any Linux-based infrastructure easily, and reduce the risk of mismanagement that comes with static SSH keys and manual sharing and rotation.
End manual key management
Generate, distribute, and manage SSH keys. Rotate them effortlessly with a single command.
Connect any device
SSH from any device and across operating systems. Answer an on-call emergency from anywhere.
Leverage SSO with MFA
Keep your existing identity provider (IdP) and multi-factor authentication for streamlined and secure access.
Upgrade to a modern Business VPN

Stay secure by default
Keep firewall ports closed, connections open—all under your direct control. Tailscale encrypts everything end to end via WireGuard’s point-to-point tunnels.
Get started in just three minutes
Connect your team in minutes with no complex configs. Seamlessly integrate with your existing infrastructure for secure access at your fingertips.
Gain speed and security
Stay secure without sacrificing performance. Tailscale is built on WireGuard® for encrypted connections without the friction of traditional VPNs.
Connect your team anywhere
Keep your team securely connected whether they’re in the office, working remotely, or on the go. Tailscale works worldwide for teams of all sizes.
Pricing that works for everyone
For individuals who want to securely connect personal devices, for free.
For small teams seeking an easy-to-use and quick-to-deploy secure network access solution.
For growing teams seeking advanced service/resource-level networking and identity-aware access controls.
For organizations seeking advanced user and posture management, robust compliance, and dedicated support.
FAQ
Read our frequently asked questions or talk to a Tailscale team member to learn more. Over 9,000 Engineering and IT teams use Tailscale’s networking software to secure their work, reduce developer disruption, and protect critical infrastructure.
What do I need in place to set up a secure VPN for a remote workforce?
Setting up a Business VPN requires careful planning and consideration of several factors, including:
- Network architecture: The VPN should be integrated into the organization’s existing network architecture.
- Security protocols: The VPN should use secure protocols such as SSL/TLS or IPsec to encrypt internet traffic.
- Authentication: The VPN should use multi-factor authentication to ensure that only authorized users can access the company network.
- Network segmentation: The VPN should be configured to segment the network into different zones, each with its own access controls and security policies.
- Monitoring and maintenance: The VPN should be regularly monitored and maintained to ensure that it is functioning correctly and securely.
How do I connect to a network from home?
Check out our docs.
