The Future of IoT and Remote Access: The Evolving Role of VPNs
If you’re going to use IoT devices, it’s crucial to secure them. This article explains the benefits of using a VPN to safeguard your IoT ecosystem and how incorporating an advanced VPN mesh network like Tailscale into your IoT infrastructure elevates security and streamlines connectivity.
If you hear the term internet of things (IoT), it probably conjures images of devices seamlessly connected to the internet, working harmoniously to simplify our lives. And indeed, that’s exactly what these devices do.
Whether you think of smart homes or smart factories, the benefits of IoT devices are extensive, from boosting efficiency and cutting costs to enhancing decision-making and elevating our quality of life.
Yet, the convenience these digital wonders bring can also make you more vulnerable to cyber threats. The more devices you expose to the internet, the more opportunities you provide for attackers to infiltrate your networks.
If you’re going to use IoT devices, it’s crucial to secure them. This article explains the benefits of using a VPN to safeguard your IoT ecosystem.
Why You Need a VPN Solution for Your IoT Devices
Among all the business VPNs on the market, VPNs with a mesh network architecture offer several advantages when it comes to safeguarding your IoT devices.
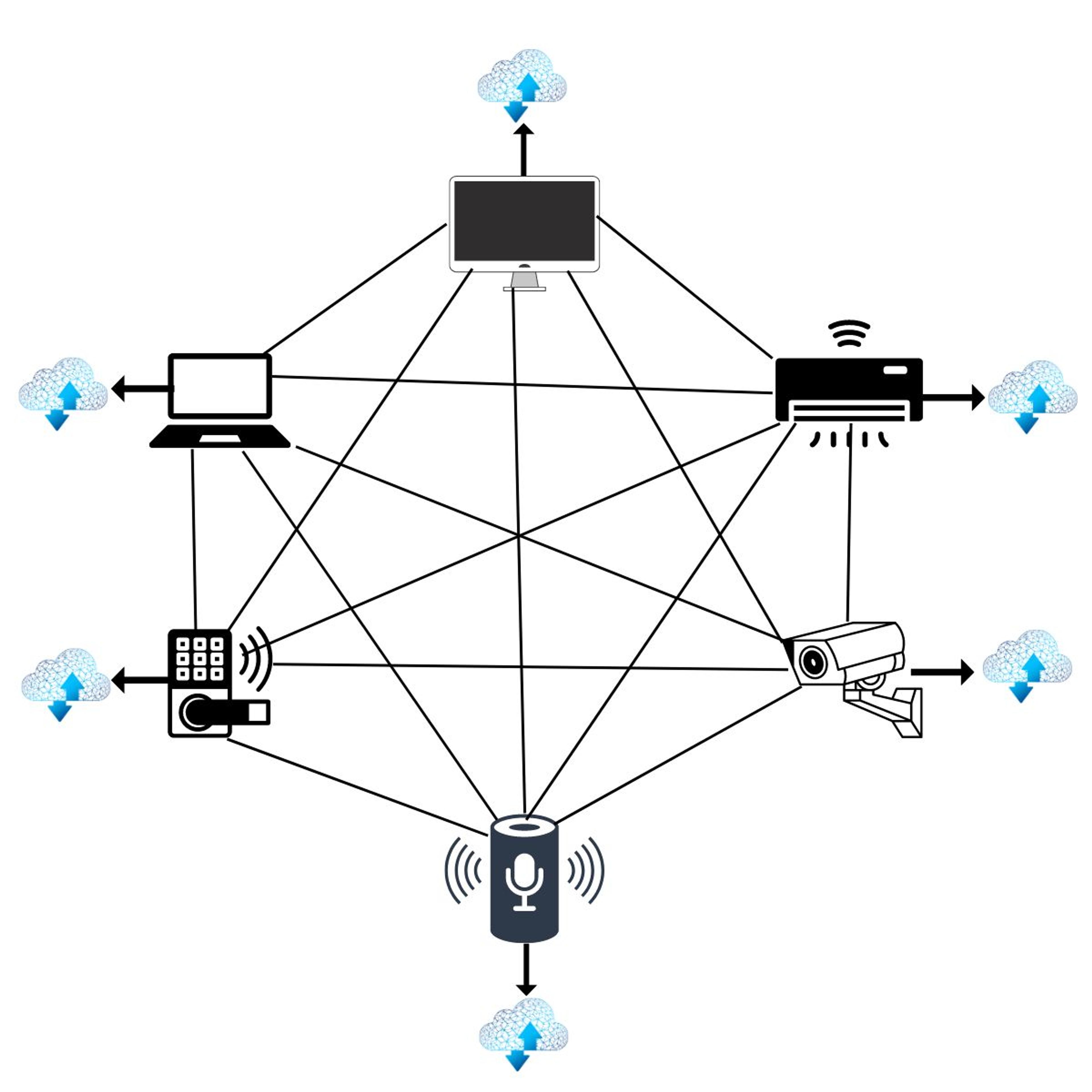
A mesh VPN is a dynamic peer-to-peer networking model that interconnects devices to form a robust and secure fabric. Within this architecture, each device acts as a node that facilitates direct communication between devices without relying on a central hub, like a VPN concentrator .
Connecting your IoT devices through a VPN network encrypts your communications to enhance security. While the devices still interact with the wider internet, the VPN shields the actual content of their data, making them more resistant to cyber threats.
Furthermore, the mesh architecture streamlines communication between devices across different networks. This simplified structure offers greater fault tolerance, better performance , and produces effective logs for near real-time monitoring, all of which help to surface irregularities and potential security vulnerabilities faster.
Benefits of Using a VPN for IoT
Using a VPN network to secure your IoT device’s traffic has many benefits:
- Enhanced privacy and security: IoT devices often transmit sensitive data over the internet, including personal information and device credentials. A secure VPN network encrypts the data exchanged between IoT devices and the user’s device to ensure privacy and protect against unauthorized access.
- Protection against man-in-the-middle attacks: Because a VPN network creates a secure channel for communication between IoT devices and the user’s device, it prevents attackers from intercepting and tampering with the data being exchanged, mitigating the risk of man-in-the-middle attacks.
- Secure remote access: VPNs allow users to securely access their IoT devices from anywhere in the world. Whether it’s monitoring and controlling smart home devices or managing industrial IoT systems for a business, a VPN ensures secure—and encrypted—connectivity.
- Network segmentation: You can use VPNs to segment IoT devices into isolated networks, separating them from a user’s main network. This provides an additional layer of security by limiting the potential attack surface and reducing the risk of unauthorized access to other devices or data on the user’s network.
- Compliance and regulatory requirements: Many industries, such as healthcare and finance, have strict regulations regarding data privacy and security. By using a secure VPN network to access IoT devices, organizations can meet compliance requirements and protect sensitive data.
- Minimizing IoT device exposure to the general internet: When IoT devices are directly connected to the internet, they can be susceptible to attacks such as port scans and DDoS attacks. Using a VPN to access IoT devices means they can be shielded from the general internet since it provides a secure and encrypted tunnel between devices.
How a VPN Better Enables and Secures IoT Devices
Incorporating an advanced VPN mesh network like Tailscale into your IoT infrastructure elevates security and streamlines connectivity.
Tailscale empowers you to establish secure access to your IoT devices through a range of authentication methods enabled through integrating your existing identity provider, including single sign-on (SSO), and multi-factor authentication (MFA). This ensures that only authorized users can engage with your devices, bolstering protection against various attack vectors.
Moreover, Tailscale seamlessly connects your devices across diverse networks, eliminating the complexities of cross-network communication. This means your IoT devices can communicate effortlessly, even across different networks or geographical locations, without requiring extensive technical know-how from you.
In less than five minutes, you can successfully set up a Tailnet with three devices located in remote places.
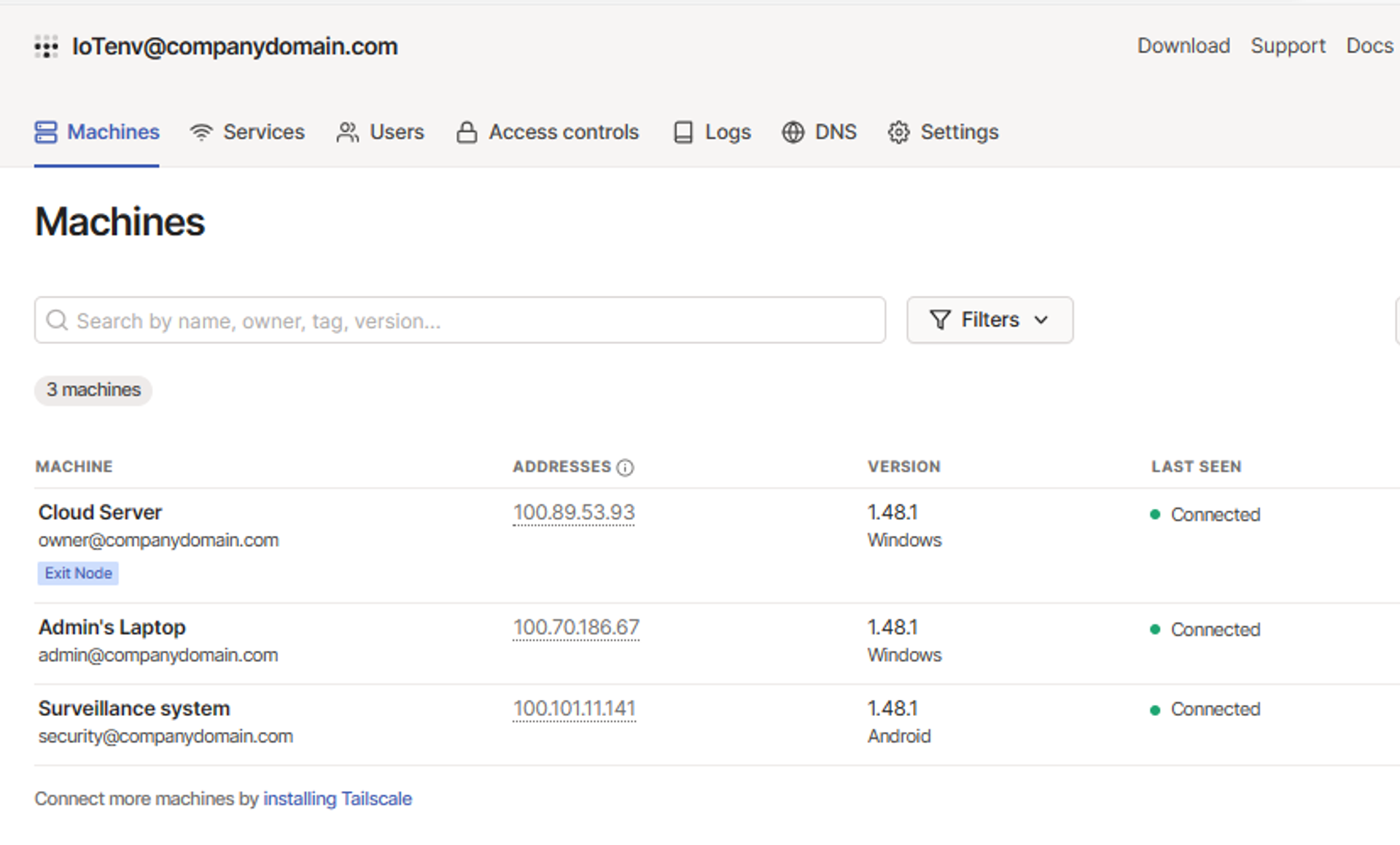
You can install Tailscale directly onto devices equipped with compatible operating systems for a hassle-free setup. Because Tailscale is integrated directly into your devices, the need for intricate configurations or technical expertise is eliminated. This zero-configuration VPN connection to your private Tailnet not only expedites deployment but also ensures that each IoT device is only visible and accessible to other authorized devices within the same network.
If any of your devices are incompatible with direct installation, Tailscale provides an alternative: subnet routers. Subnet routers act as intermediaries that facilitate communication between incompatible devices and your Tailscale network. This bridging mechanism ensures that every device within your IoT ecosystem can be incorporated into your secure network, regardless of its inherent compatibility limitations. As an additional perk, devices behind a subnet router do not count towards the device limit of your Tailscale plan.
Tailscale also simplifies the management of complex security tasks for both administrators and users.
For administrators, Tailscale automates key rotation, consistently updating encryption keys without requiring manual intervention. This eliminates the burden of manual key management, allowing for a more streamlined operation.
For users, Tailscale integrates with your existing identity provider This not only enhances security but also simplifies the login process, allowing users to rely on a single, familiar authentication workflow . The integration brings the dual benefits of bolstered security and greater convenience for all parties involved.
Conclusion
By streamlining operations at home and at work, IoT devices offer convenience and efficiency. However, with this convenience comes a downside. The fact that they’re connected to the internet and each other means a bigger surface attack for potential cyber threats.
VPNs are a powerful way of safeguarding the integrity of IoT ecosystems against such threats. The VPN mesh network architecture, in particular, secures communication between IoT devices, which enables direct and secure communication between devices to minimize their exposure to potential threats.
Tailscale streamlines your IoT setup with its zero-config approach. Once you install the software on a device, it seamlessly becomes part of your tailnet without requiring you to manually adjust firewalls or open specific ports with NAT Traversal.
A VPN solution like Tailscale not only adds strong security to your IoT network; it also simplifies the connection process for these devices with features like single sign-on and multi-factor authentication, integration with existing identity services, and zero-configuration across multiple operating systems.
To read more about how Tailscale works, check out the documentation or sign up for a free trial to try it out yourself.






