Thanks for signing up for the JIT Network Access Webinar
Take the next step and get started with Tailscale. It only take five minutes to connect your first device. (Really, it's that easy.)
Secure access, when and where you need it
Tailscale makes secure access effortless. Just-in-Time (JIT) access gives your team what they need – only when they need it – without always-on VPNs or extra risk. Simple to deploy, built on WireGuard®, and works with your existing tools.
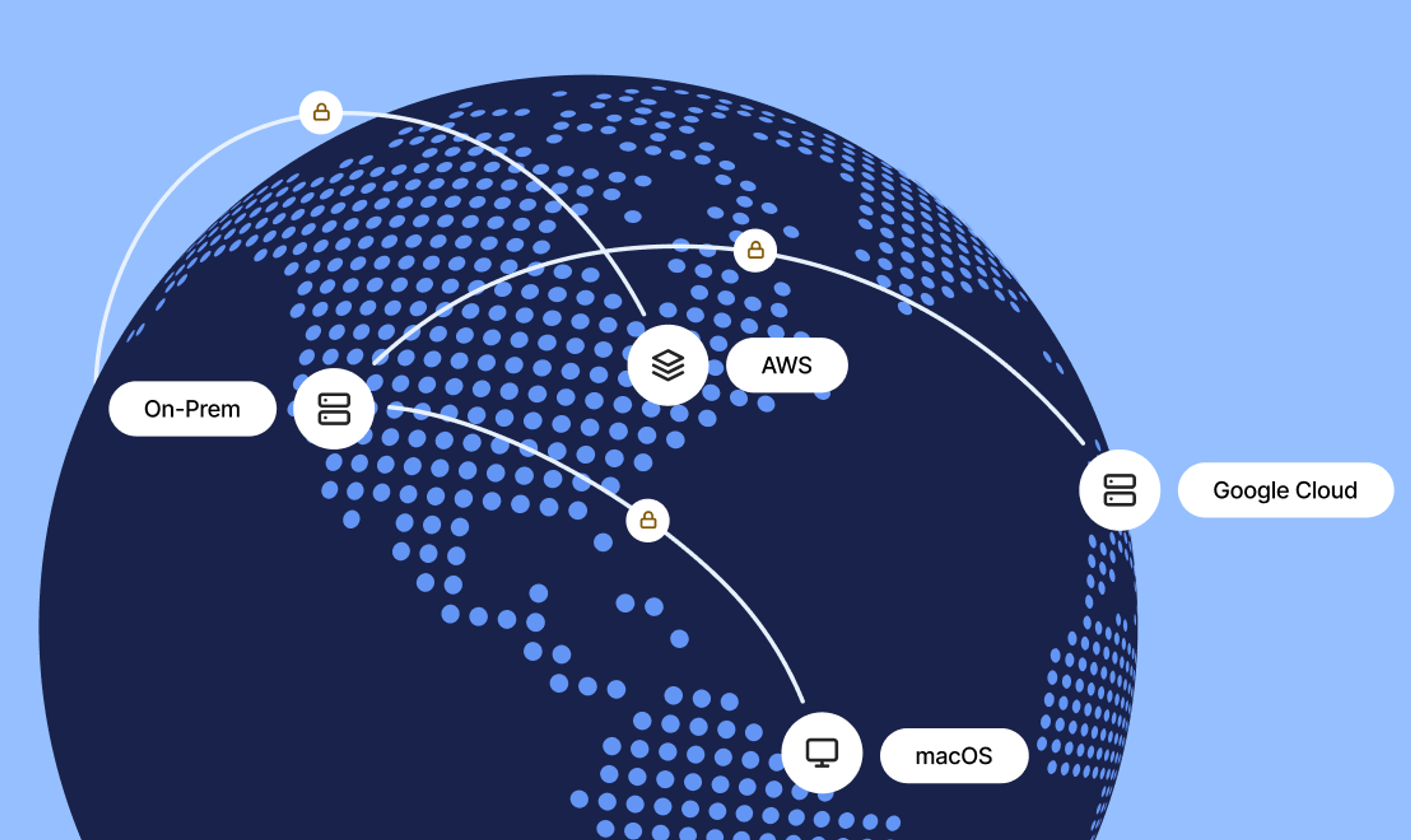
Bringing Tailscale to work has never been easier
Bringing Tailscale to work is the easiest way to simplify secure remote access for your team. Whether you need to connect to internal tools, file shares, or cloud infrastructure, Tailscale makes it seamless – no VPN headaches, no complex firewall rules.
Trusted by 10,000+ companies




Get these features and more with Tailscale
ACL groups
Easily manage access with auto, custom, or provisioned groups – no manual updates needed. Keep teams connected while ensuring the right people have the right access.
GitOps for ACLs
Easily modify, review, and roll back JSON-based configurations directly from GitHub or GitLab, ensuring seamless, version-controlled security and simplified access management.
Bring your own IdP
Secure access with your existing identity provider. Tailscale supports SSO and MFA across a wide range of IdPs, including custom OIDC providers, for seamless authentication.
Mesh capabilities
Enable direct, secure device-to-device connections, even across complex NAT gateways. Enjoy faster, more reliable connectivity without relying on a central VPN server.
End-to-end encryption
Every connection is secured with WireGuard’s end-to-end encryption, ensuring your data stays private and protected. Tailscale keeps security simple – no configuration needed.
Scoped keys
Generate scoped, case-sensitive keys for secure API access and automation. Tailscale supports Auth keys, OAuth clients, SCIM API keys, Webhook secrets, and more.
Audit logging
Gain full visibility into your network with audit logging. Track who did what and when, with detailed insights into actions, target resources, access history, and security events.
Log streaming
Seamlessly stream network flow and audit logs to your preferred SIEM provider. Keep security teams informed with real-time visibility into network activity, access, and potential threats.
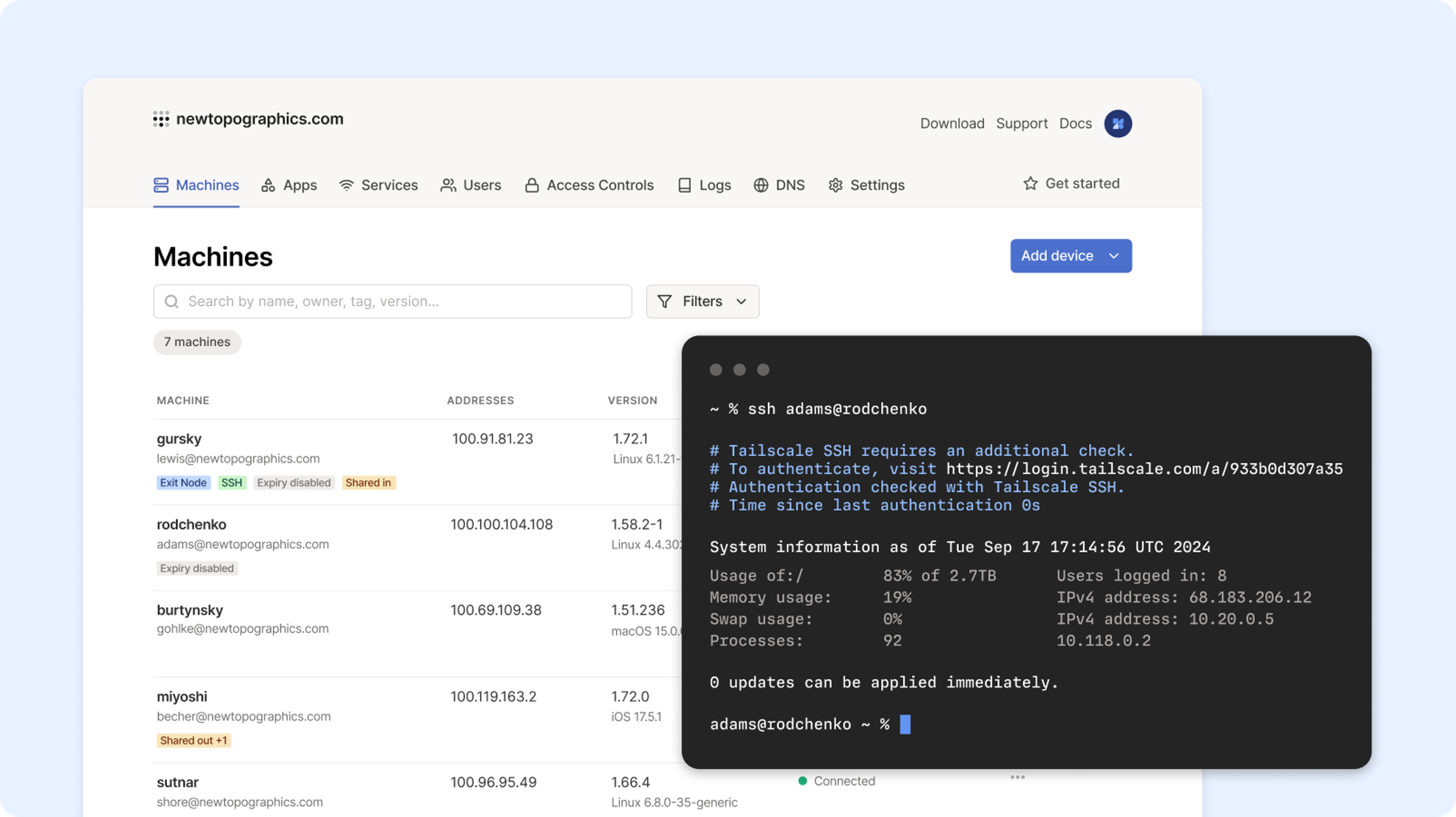
Tailscale SSH (with recording)
Securely access and record SSH sessions without managing keys. Tailscale SSH enables audited shell access – no bastions or shared credentials needed.
Pricing that works for everyone
For individuals who want to securely connect personal devices, for free.
For small teams seeking an easy-to-use and quick-to-deploy secure network access solution.
For growing teams seeking advanced service/resource-level networking and identity-aware access controls.
For organizations seeking advanced user and posture management, robust compliance, and dedicated support.
