Daniel Kerwin joined Gini, a market-leading company for payment solutions and intelligent data extraction from documents, eight years ago. Since then, Gini has grown substantially, and Daniel is now Gini’s Head of Technical Operations. He and his team handle many responsibilities, from enabling developers, to security, to devices and organizational development. Daniel describes his role at Gini as, “If there’s bits and bytes coming in and out of it, I have some form of contact with it.”
Previously, Gini was using a regular, corporate standard VPN and struggling to add two factor authentication, device management across multiple operating systems, certificate updates, and key rotation to their already complicated setup.
Daniel read our blog post explaining How Tailscale Works, and found it so compelling that he installed it on his home network. The next day, Daniel ended his VPN research and installed Tailscale in a test environment in the company. It gained traction and Tailscale solved many of their pain points and simplified their setup. It was a big relief.
“Getting our entire system up and running on Tailscale, I was a little secretive for the first couple of days. But I think the company as a whole was basically using it in the first month. We did some tests, but once we were satisfied, all it took for our team was to download the client and log in with their existing Google account. That’s it.”
Before Tailscale, Troubleshooting was Tricky and Time Consuming
Previously, Gini was using the open source version of OpenVPN and struggling with one of their company’s main requirements: two factor authentication.
With the corporate VPN, the process required compiling a library manually, distributing it to each affected machine, and keeping it up to date. With multiple machines in many different locations, it was complex to perform updates across the board.
Gini ran a complex setup with overlapping networks and routing configurations with multiple tunnels on each VPN gateway. Synchronizing all that was already complicated, but to make it worse, having different device classes and operating systems, with some people working from an iPad, other people working from a MacBook or a Linux laptop, each with different VPN apps and configurations, was a lot of overhead to manage. With the old system, figuring out why something didn’t work was getting trickier and more time consuming.
After reading a blog post explaining How Tailscale Works, Daniel tried it out at home before bringing it to work. Tailscale ticked all Gini’s boxes by removing the pain points and problems they were facing, to add support for two-factor authentication across their applications, device approval, and to easily update remote machines regardless of platform. The team also experimented with Wireguard as a replacement for OpenVPN but key management and lack of tooling around it made it difficult to switch right away. Once they discovered Tailscale, the company as a whole was using it in the first month. It was a big relief.
SSH and VPN credential theft is a security hazard, and manually rotating keys was a time sink on Gini’s old VPN. Daniel and his team love the way key rotation works automatically with Tailscale.
The approach Tailscale takes is to authenticate each device and person combination with a separate private key; that way, if a credential is stolen, you always know from where. Each device can rotate that device-specific key as often as it wants, since the private key only lives in one place (on the device), and the public keys are all distributed rapidly from our coordination server to every other device that needs them.
Because of this highly consistent key rotation (which is hard to implement with ssh keys or passwords), Tailscale always knows exactly when a particular keypair has been retired. If that keypair makes a surprise reappearance, it must mean credential theft, which means a potential breach, which can then be further investigated.
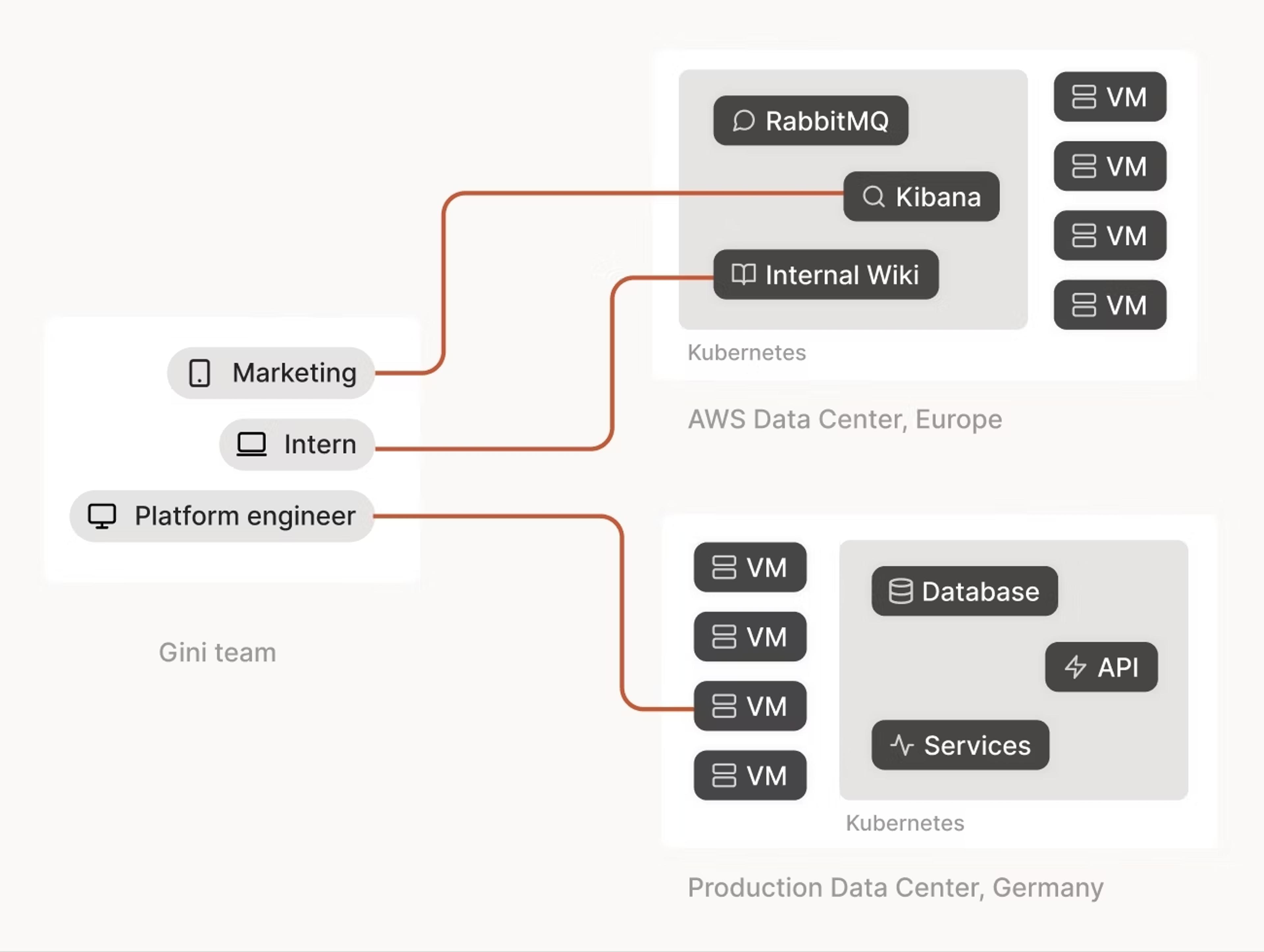
Everyone at Gini uses Tailscale now, with access control lists (ACLs) varying access levels based on each person’s identity and groups: for example, an intern can access the wiki, while a platform engineer can access production servers. With ACLs, Gini reports that they have fine grained control over what each team can access. Compared to the coarse firewall rule sets in the old VPN that required people to switch from one tunnel to another as their role changed, Tailscale’s identity-based ACLs are much easier to create and audit.
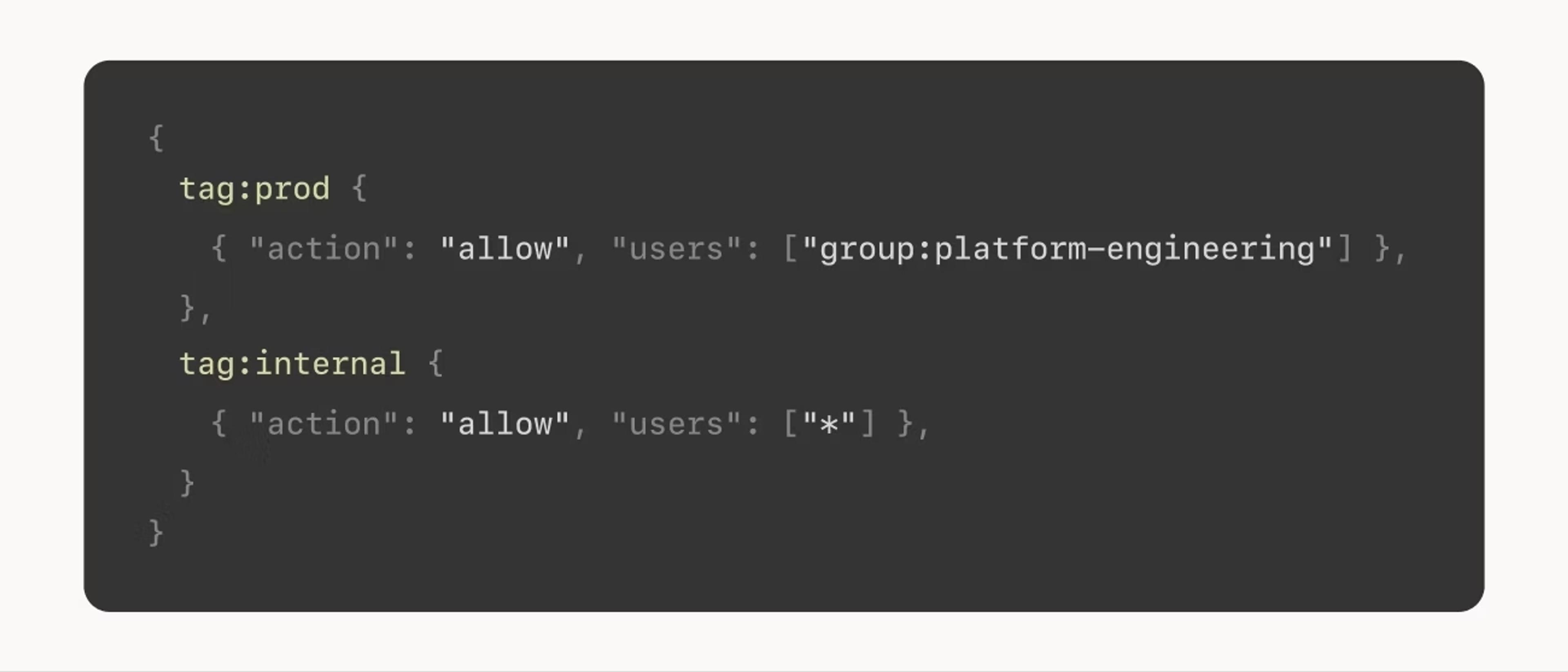
Getting started with Tailscale was seamless, allowing Gini to use the Google accounts they already rely on without any extra effort. Sign up was easy with their existing Google two factor authentication and everything worked consistently, even while running on multiple devices and platforms.







