Zero Trust would be easy to implement, were it not for all those pesky humans.
As part of Tailscale’s report on the State of Zero Trust in 2025, Tailscale commissioned a survey of 1,000 IT, security, and engineering leaders, seeking to understand where their organizations stood in implementing secure access and adopting a true Zero Trust environment. The survey asked respondents what they wanted, what policies they were actually implementing, and what—or, often times, who—was blocking a real Zero Trust strategy.
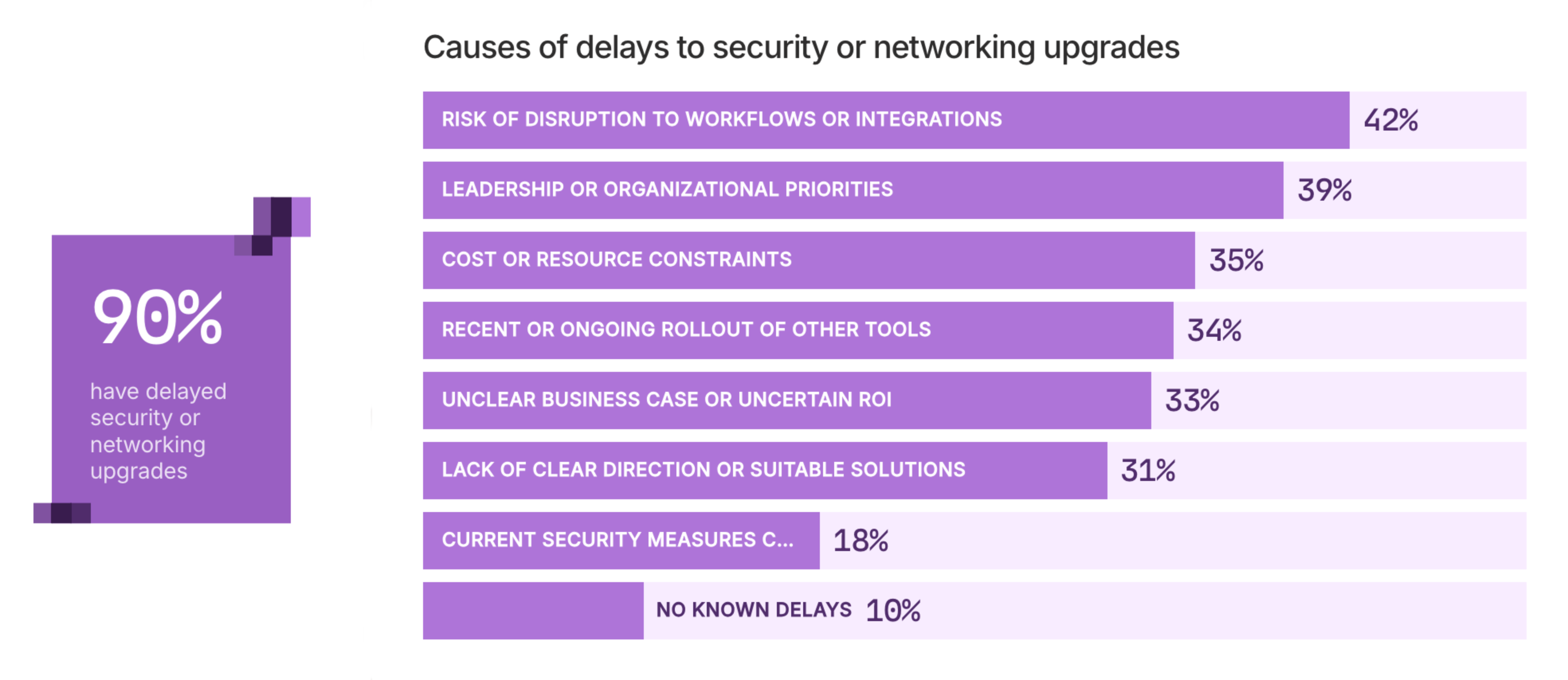
Take security upgrades, for example. Why might networking and security upgrades have been delayed? 42% of those surveyed cited a “risk of disruption to workflows or integrations.” Another 39% (given multiple options to select) picked “leadership or organizational priorities.” One-third pointed to an “unclear business case” or an uncertain return on investment (ROI). And 31% suggested a “lack of clear direction or suitable solutions.”
Whatever the cause, when people encounter the slow, overly complicated security systems set up by other people, they can do some rather dangerous things. 83% of all respondents said they circumvented security measures to get things done, be it sharing credentials (23%), using unapproved software (28%), or resorting to “I’ll just use my personal device” (32%).
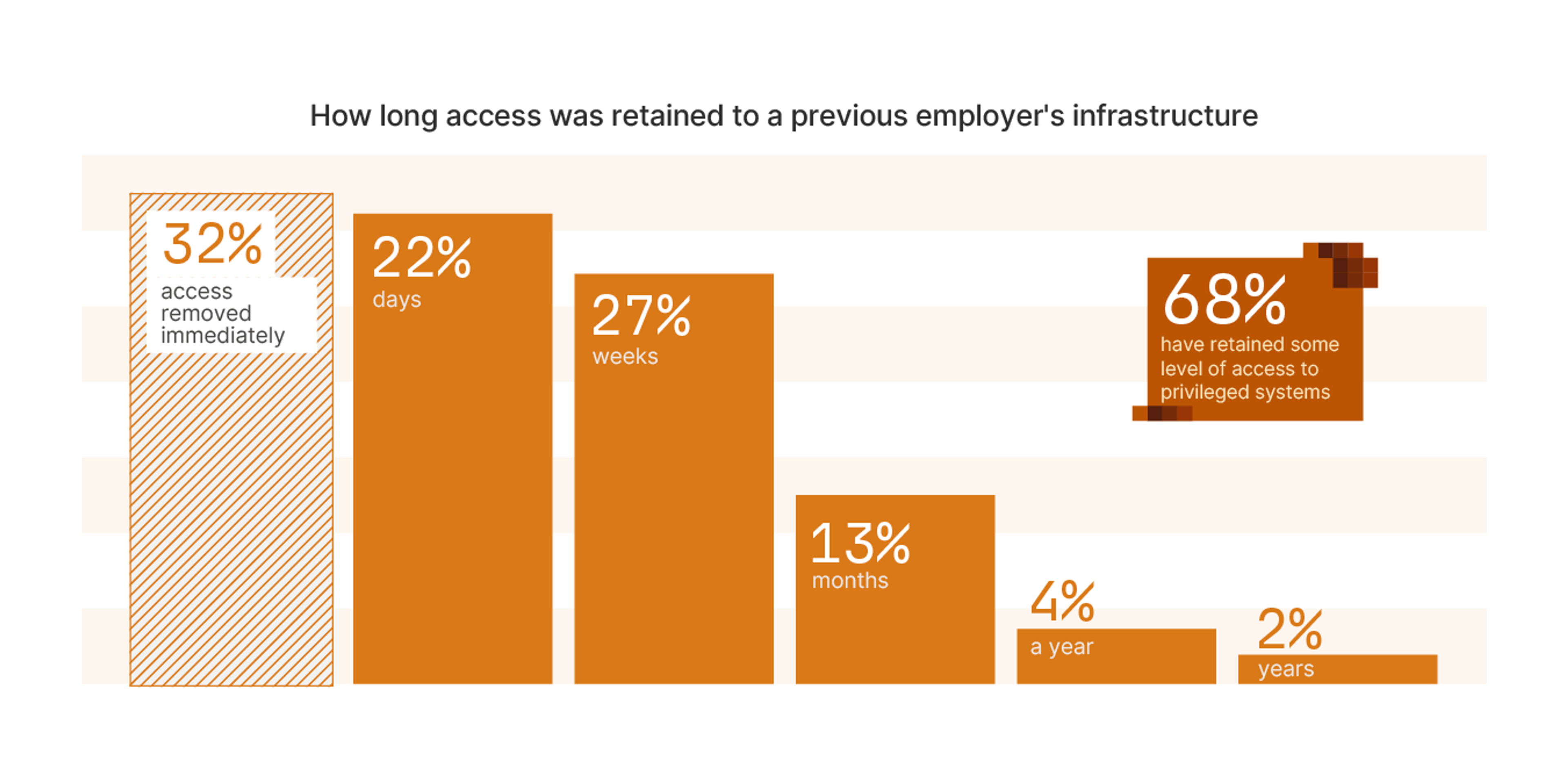
And those are just the current employees; the report has some eye-opening stats on how a majority of those surveyed retained some access to privileged systems after they left other jobs.
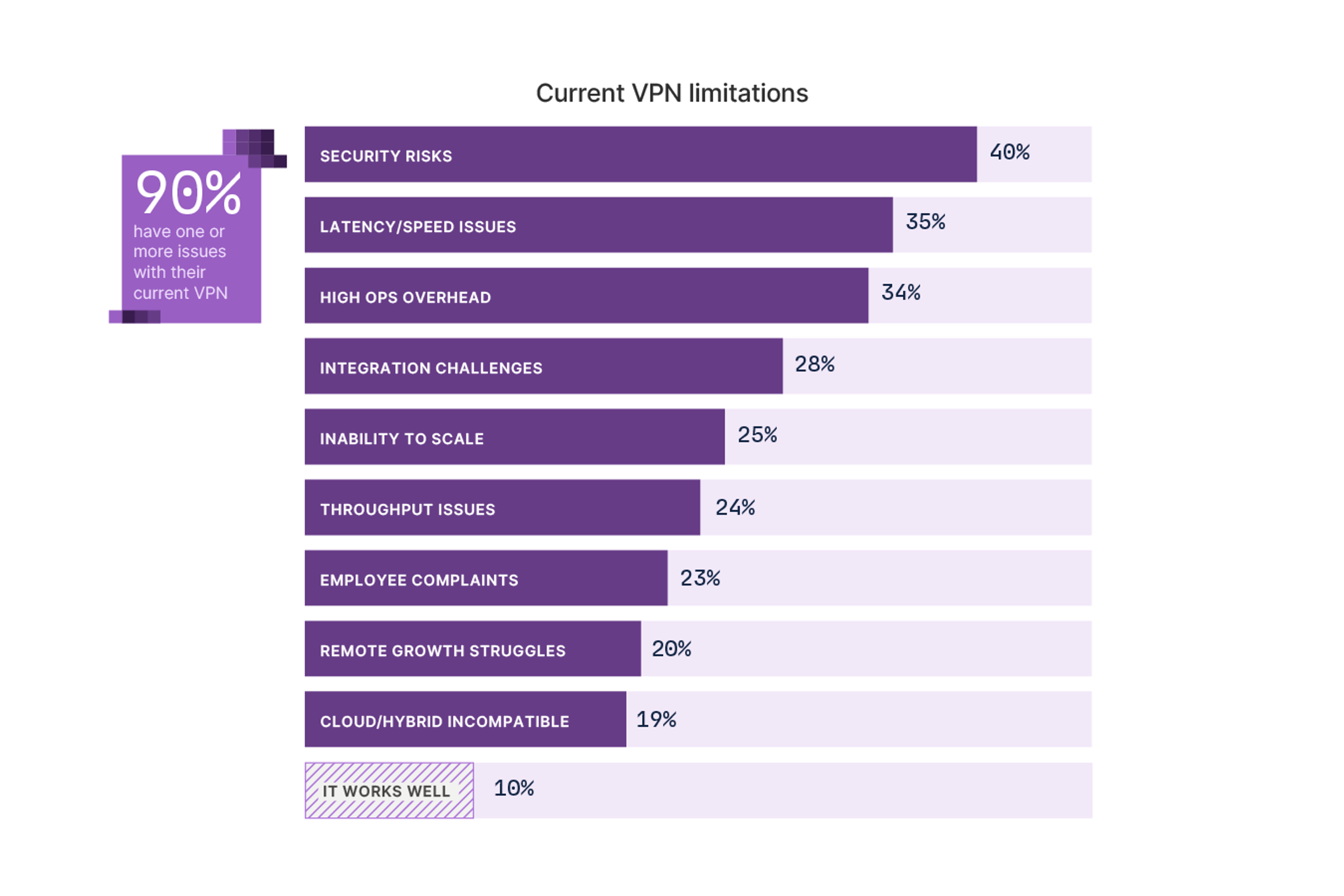
Many companies lean on legacy VPNs to defend against such oversights and failures, hoping to limit access to just the right things. How is that working out? Roughly 90% of those people surveyed reported one or more notable issues with their current VPN solutions. Maybe that’s not surprising, given that nearly 70% of them involve manual (read: human-driven) provisioning.
While people will always find ways to be a problem, they’re also key to real Zero Trust solutions. Identity-native access, based on users and their authenticated devices instead of network location, is a pillar of Zero Trust systems. With an identity-centric access scheme, turning off an ex-employee’s account immediately revokes all related permissions. Eliminating lingering access closes security gaps and addresses compliance requirements. And building granular access controls based on users, not networks, creates the kind of consistency that Zero Trust demands.
For more insights into the challenges and rewards of building a Zero Trust system, read the full report in on our website, where you can explore interactive graphics and download a full PDF version. All humans are welcome.


 Kevin Purdy
Kevin Purdy




