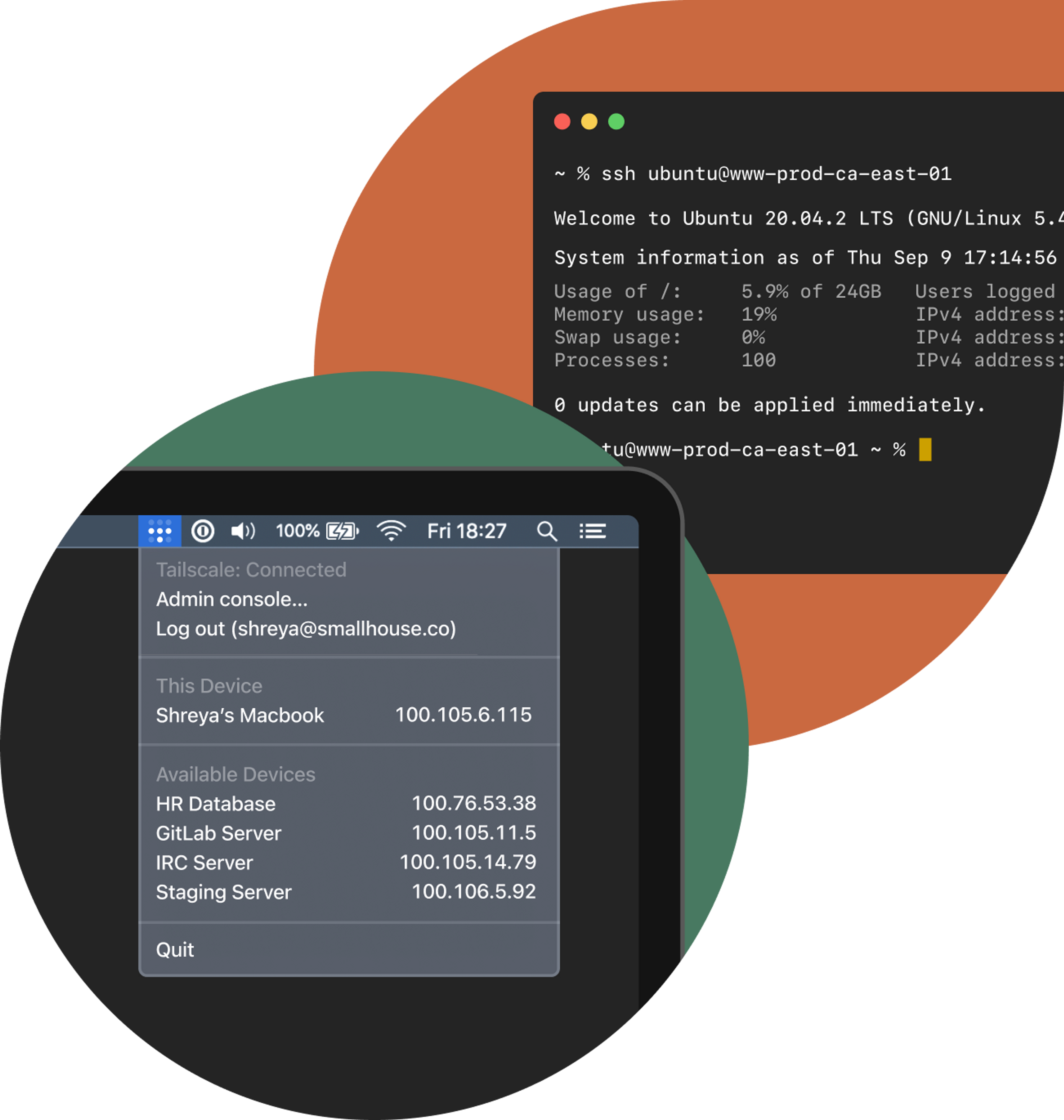
SSH but make it Tailscale
No additional hardware to manage. No complicated firewall rules. Tailscale keeps it secure.
SSO and MFA
Use your existing identity provider and multi-factor authentication to protect SSH connections. Protect SSH connections the same way you authorize and protect application access.

Built-in key rotation
Rotate keys with a single command. Tailscale does the key distribution. Each server and user device gets its own node key, used for authenticating and encrypting the Tailscale connection. Follow key management best practices and rotate keys frequently. Node keys can be rotated by re-authenticating the device, as frequently as every day.

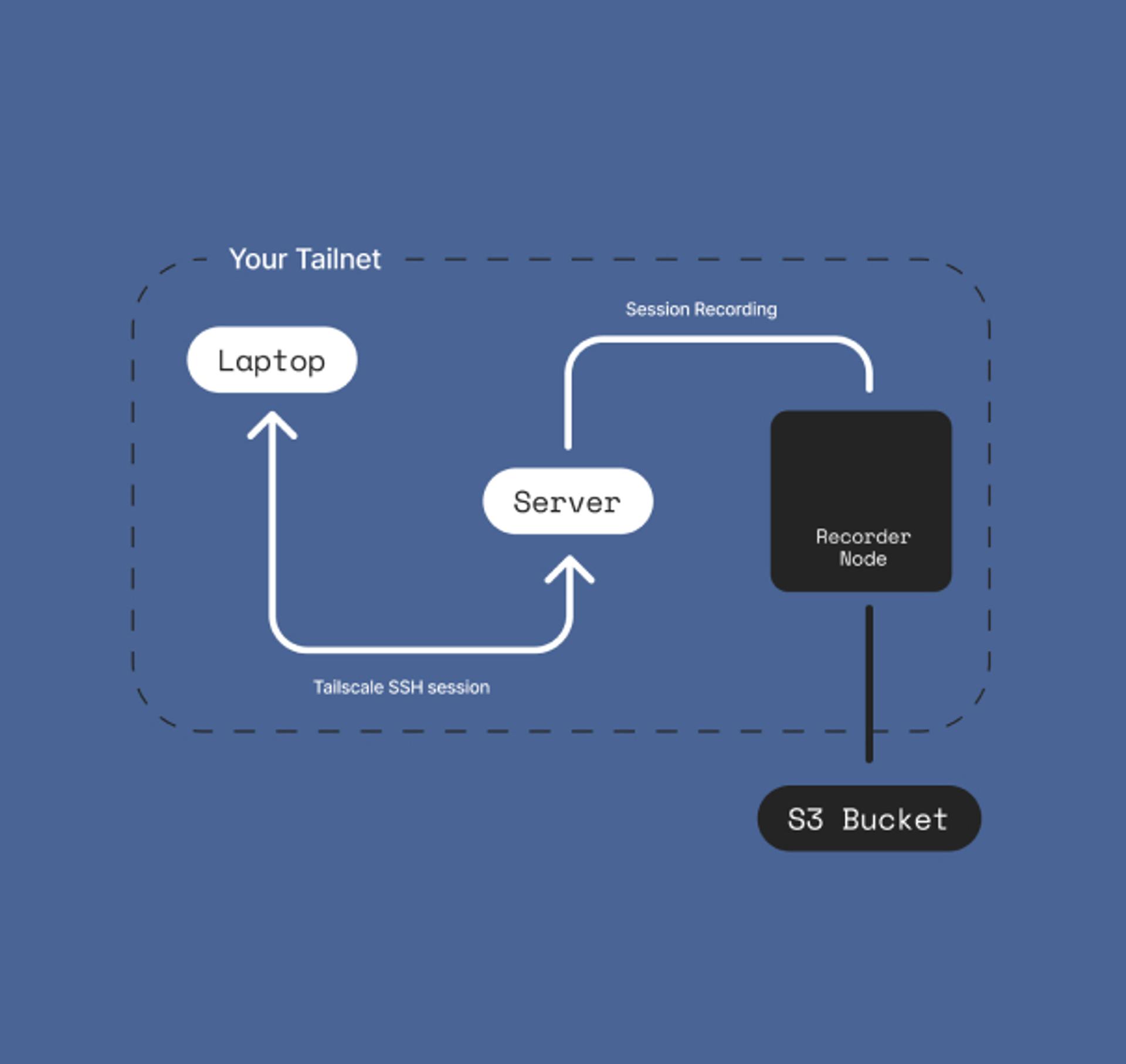
Enable SSH Session Recording
Whenever a Tailscale SSH connection is initiated, store terminal output recording in any S3 compatible service or local disk to aid in security investigations, and meet compliance requirements.
Connect to, and from, any device
SSH even from your mobile devices, and across OSes. Tailscale SSH works where Tailscale works. Code from an iPad to your Linux workstation, without having to figure out how to get your private SSH key onto it. Answer an on-call emergency from anywhere, which means you can leave your desk now.

Access servers without publicly exposing them
Unlike bastion hosts, you don't need to funnel all your traffic through a single, demarcated network entry point. As long as there's a way, Tailscale will find how to connect to your server.

Reduced latency with point-to-point connections
Connect directly from your device to your server, without having to hairpin through a bastion. Connect wherever you work, without slowing down by routing traffic through head office.

Authentication and encryption
Use SSH keys unique to your tailnet
Manage permissions as code
Define what connections to your devices you want to allow using a standard syntax. Understand your SSH access controls in a centralized configuration file.

Revoke SSH access easily
Revoke access to SSH to a machine almost instantaneously by updating Tailscale ACLs. When an employee offboards, be confident their SSH key won't allow access to critical infrastructure.

Add a user or server painlessly
Maintain users and servers in your network without snowballing complexity. When you welcome a new employee, you don't need to touch every machine to update access. When you provision a new server, use ACLs to give the right people access and add it to your team's known hosts.

Works with what you're already using
Mac, iOS, Windows, Android or Linux — even your Raspberry Pi. Tailscale works wherever you do.
Mac
iPhone & iPad
Windows
Android
Linux





