Share your nodes with other users
You can share access to specific machines with people outside your tailnet without exposing them to the public internet. Sharing gives the recipient access to only the shared device in your tailnet, and nothing else. It respects the ACL and MagicDNS settings of both your tailnet and the recipient's tailnet. Sharing strips ACL tags, groups, and subnet information from the recipient tailnet. A shared node is visible only to the individual recipient user—it is not visible to the recipient user's entire tailnet.
Share a machine with another user
You need to be an Owner, Admin, or IT admin of a tailnet to share a node.
To share a machine:
- Open the Machines page of the admin console and find the machine you'd like to share.
- Send invites via email or manually via links.
- Wait for the recipient to accept.
After the recipient accepts the invite, they can access the shared device from their Tailscale clients and admin console, as if it was on their own tailnet. For example, the macOS app will display it in the menu bar, and Linux apps will see it from tailscale status.
Notes about shared machines:
- Shared machines have the same IP address on the original tailnet and the other user's tailnet. When you share a machine, you can provide the machine's Tailscale IP addresses in advance, and the recipient can use it.
- Tailscale quarantines shared machines by default. A shared machine can receive incoming connections (from the other user's tailnet) but cannot start connections. This means users can accept shares without exposing their tailnet to risks.
- As of Tailscale v1.4, shared machines appear in the other tailnet as the sharer, not the owner of the device. If Ross shares his co-worker Dave's device to another tailnet, it will appear to be owned by Ross in the new tailnet.
- Unused invite links expire after 30 days.
Share using email
When you send invites via email, each specified recipient receives a single-use invite link to your device. The recipient does not need to have a Tailscale account with the same email address. They can log in and accept the share from any Tailscale account.
- Select the
menu, then select Share to open the Share dialog.
- Select Share via email tab.
- Add the email address for each user that you want to send invite links.
- Select Share to send email invitations to each listed email address.
Share using link
For invite links you plan to share manually, you can choose to make a single-use or reusable invite link. A single-use invite link is a one-time use link. A reusable invite link can be used up to 1,000 times. Unused links expire in 30 days for both single-use and reusable invite links.
- Select the
menu, then select Share to open the Share dialog.
- Select Copy invite link tab.
- (Optionally) toggle on Reusable link for a link that can be accepted more than once.
- Select Copy share link to create the link and copy it to your clipboard.
- Share the copied invite link to your intended recipient. Treat the invite link the way you would a password. It provides the ability to connect to a machine within your tailnet.
Wait for the recipient to accept
You need to be an Owner, Admin, or IT admin of a tailnet in order to accept a shared node.
The recipient can visit the invite link to review your invitation. After they accept, you can see their profile picture and email address in the Share dialog. You'll also see an indicator in the Machines list on the admin console showing which machines have been shared to external users.
Revoke an invite
You can revoke a share or share invite from the Machines page of the admin console. After you revoke an invite, the recipient user can no longer access the shared device. To restore access, you must create a new invite and the recipient must accept that new invite.
To revoke an invite:
- Go to the Machines page of the admin console.
- Select the Share option for the machine.
- Select the
menu > Revoke invite.
How sharing works
Sharing a device exposes that device to a user on another tailnet. Only that user is able to see and access your device. It is invisible to other users on that tailnet.
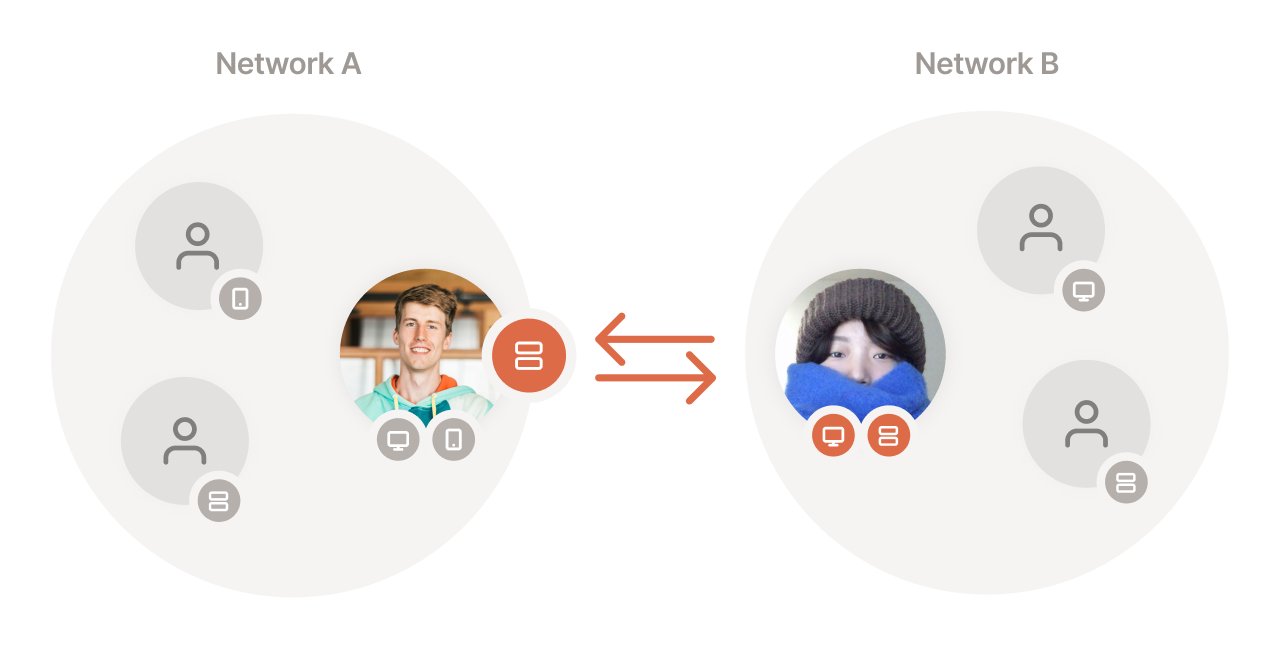
In this example, only the shared device from tailnet A and the share recipient's devices in tailnet B can talk across tailnet boundaries.
When you accept an invite, Tailscale exposes the minimum set of information possible about your tailnet to that device. Accepting a invite exposes:
- The email and avatar of the recipient (required to help confirm invites)
- Physical device IPs of machines from your tailnet (required for connections)
Quarantine
Shared devices are quarantined by default. They can respond to incoming connections from the tailnet they're shared to, but cannot initiate connections on their own. Quarantining helps sharing be "secure by default", since you can accept shares with no risk of exposing your tailnet.
Sharing and MagicDNS
MagicDNS is a per-tailnet setting. If your tailnet has MagicDNS enabled, you can access devices over MagicDNS regardless of the other tailnet's settings.
Shared devices support MagicDNS in Tailscale v1.4 or later. Shared devices can only be reached by using their fully qualified domain name, which looks like <hostname>.<tailnet-name>.ts.net.
<hostname>is the machine name of a device.<tailnet-name>is the tailnet name of a tailnet.
For example, if your friend shares a device named minecraft-server on the yak-bebop tailnet to your tailnet, you can reach it at minecraft-server.yak-bebop.ts.net. However, you can't reach it at minecraft-server from your tailnet.
Previously, you might have used a tailnet name ending in .beta.tailscale.net. If so, migrate to the new tailnet name
that ends in .ts.net. The existing beta.tailscale.net name remains supported until at least November 1, 2023.
These restrictions are necessary to prevent MagicDNS names from changing unexpectedly, and to support future features on top of sharing.
Sharing and Access Control Lists (ACLs)
Sharing respects the ACLs of both tailnets. If either tailnet disallows connections to/from a device, no connections can be established. If you're having trouble connecting to a shared device, review your tailnet policy file for rules that might be blocking access.
To write access rules that apply to a shared device, you can use the email address of the recipient. For example, if you invite alice@example.com to share a machine at 100.74.78.2, you can give her access to a particular host.
"acls": [
{ "action": "accept", "src": ["group:admins"], "dst": ["*:*"] }
{ "action": "accept", "src": ["alice@example.com"], "dst": ["100.74.78.2:*"] }
]
Be careful of rules like "src": ["*"], which apply to everyone who has access to your tailnet, including invited users. Consider making a group that
includes all your tailnet users instead of *.
You can also write access rules by using the special autogroup:shared group. This group automatically includes all users invited to your tailnet, and lets you write rules without knowing email addresses in advance.
For example, to restrict invited users to only access webserver ports 80 and 443, you can write a rule like so:
"acls": [
// Admins can access everything on the tailnet.
{ "action": "accept", "src": ["group:admins"], "dst": ["*:*"] },
// Shared users can only access port 80 and 443 of devices they are invited to.
{ "action": "accept", "src": ["autogroup:shared"], "dst": ["*:80,443"] },
]
Remember: invited users are only able to access devices you've invited them to share. Access rules further limit what they can access. Although the rule *:80,443 seems like it allows access to all devices, it only further restricts their access to the ports we've specified.
Sharing does not expose ACL tags to the other tailnet. All tag information is stripped and cannot be used in the tailnet policy file of the other tailnet.
Sharing & Subnets (subnet routers)
Shared nodes do not advertise subnets to the tailnets they're shared into, while inviting external users into your tailnet will give them access to subnet routers.
Sharing & Exit Nodes
Sharing an exit node exposes it to the other tailnet.
To share an exit node, use the following sequence:
-
If you are not using
autoApprovers, allow the exit node from the admin console. -
Share the node per the instructions above, allowing the recipient to use it as an exit node. Ensure the Allow use as an exit node option is checked.
Sharing and exit nodes
- Revoke the share.
If you want to share the node again, share it per the instructions above and ensure the Allow use as an exit node option is unchecked.
- Advertise the device as an exit node.
- If you are not using
autoApprovers, allow the exit node from the admin console. - Share the exit node.
If a user is deleted, the shared nodes they manage will be deleted. If a user is suspended, the shared nodes they manage will not be able to connect to other devices.
Sharing and suspended or deleted users
When you delete a user, it also deletes the shared machines they manage. If you suspend a user, Tailscale prevents the shared nodes they manage from connecting to other machines.
Every time you share a node with a unique user and they accept the invitation, we'll increase the device limit on both your accounts by two. This is valid for every unique domain that accepts a node shared by you. The rewards are applied automatically when the invitation is accepted, and will be reflected in your device limits on the Billing page of the admin console
Sharing and rewards
Every time you share a machine with a unique user, and they accept the invitation, Tailscale increases the device limit on both accounts by two. This applies to every unique domain that accepts a machine you shared. The rewards apply automatically when a user accepts an invitation, and the increased device limit shows on device limits on the Billing page of the admin console.
Troubleshooting
If you can see that a machine that was shared with you, but you can't connect to it:
- If you're trying to access the device by machine name (and not 100.x.y.z address), ensure you have MagicDNS enabled. MagicDNS must be manually enabled from the DNS page.
- Review your tailnet's ACLs to see if you have any rules that might disallow access. If you don't, it's possible the tailnet that shared it with you is restricting the traffic. Ask them to review their ACLs too.